Link: https://tryhackme.com/room/poster
#1 “What is the rdbms installed on the server?“
#2 “What port is the rdbms running on?“
Use nmap to find open ports:
nmap -sCV 10.10.65.155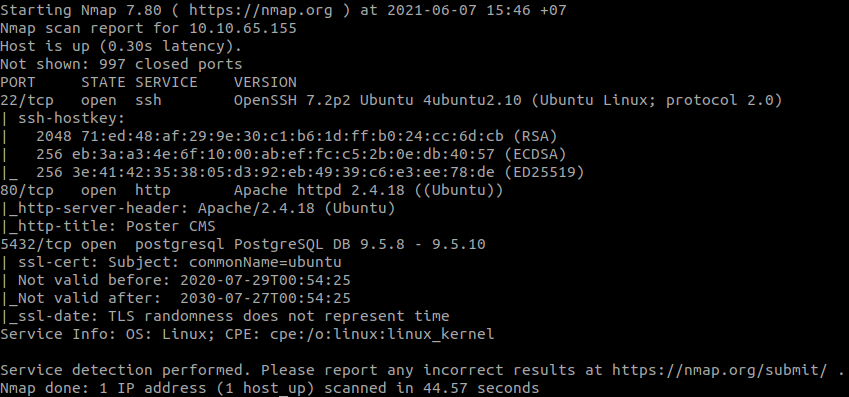
#3 “After starting Metasploit, search for an associated auxiliary module that allows us to enumerate user credentials. What is the full path of the modules (starting with auxiliary)?“
Start Metasploit and use:
search PostgreSQLThe answer is in number 7.
#4 “What are the credentials you found?“
Set RHOSTS and run.
#5 “What is the full path of the module that allows you to execute commands with the proper user credentials (starting with auxiliary)?“
Start Metasploit and use:
search PostgreSQLThe answer is in number 9.
#6 “Based on the results of #6, what is the rdbms version installed on the server?“
Set RHOSTS, PASSWORD and run.
#7 “What is the full path of the module that allows for dumping user hashes (starting with auxiliary)?“
search postgres auxiliary hashThe answer is in number 2.
#8 “How many user hashes does the module dump?“
Set RHOSTS, PASSWORD and run.
#9 “What is the full path of the module (starting with auxiliary) that allows an authenticated user to view files of their choosing on the server?“
Start Metasploit and use:
search PostgreSQLThe answer is in number 8.
#10 “What is the full path of the module that allows arbitrary command execution with the proper user credentials (starting with exploit)?“
The answer is in number 4.
#11 “Compromise the machine and locate user.txt“
After get shell, read /var/www/html/config.php, we will see a credential of alison here.
Get alison‘s shell:
su - alison
cat /home/alison/user.txt#12 “Escalate privileges and obtain root.txt“
Check what we can do with:
sudo -l
So we can run all as root.
sudo cat /root/root.txt