Link: https://tryhackme.com/room/overpass2hacked
Task 1: Forensics – Analyse the PCAP
#1 “What was the URL of the page they used to upload a reverse shell?“
Download the pcapng file, open it with Wireshark, follow TCP Stream. The answer is in Stream 0.
#2 “What payload did the attacker use to gain access?“
The answer is in Stream 1.
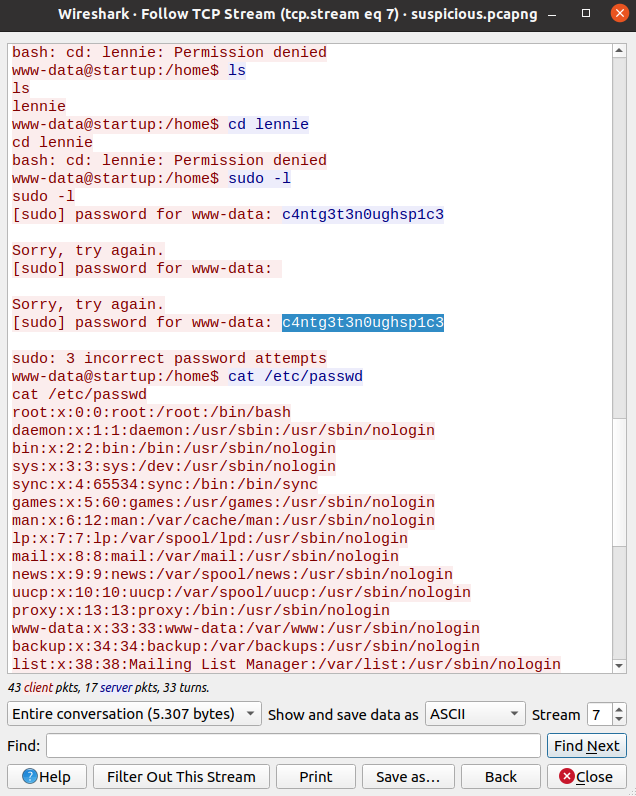
#3 “What password did the attacker use to privesc?“
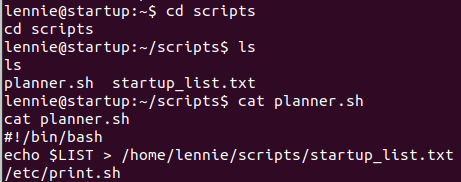
#4 “How did the attacker establish persistence?“
The answer is in Stream 3.
#5 “Using the fasttrack wordlist, how many of the system passwords were crackable?“
Save the data of /etc/shadow in Stream 3 to a file named “shadow“.
Download the fasttrack wordlist.
Next, we use JohntheRipper to crack the password.
This link tells us how to install and use JohntheRipper.
john-the-ripper shadow -w=fasttrack.txtTask 2: Research – Analyse the code
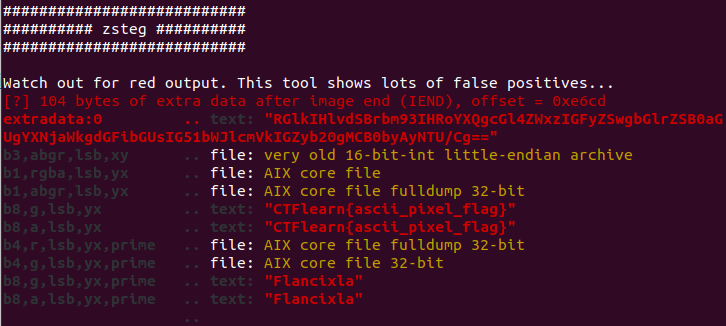
#1 “What’s the default hash for the backdoor?“
#2 “What’s the hardcoded salt for the backdoor?“
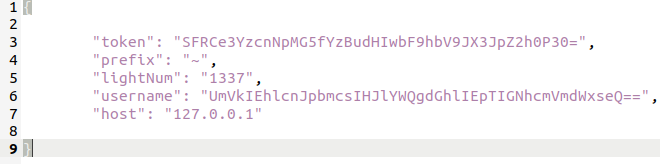
Access the github link in Stream 3 and read main.go to get the answers.
#3 “What was the hash that the attacker used? – go back to the PCAP for this!“
The answer is in Stream 3.
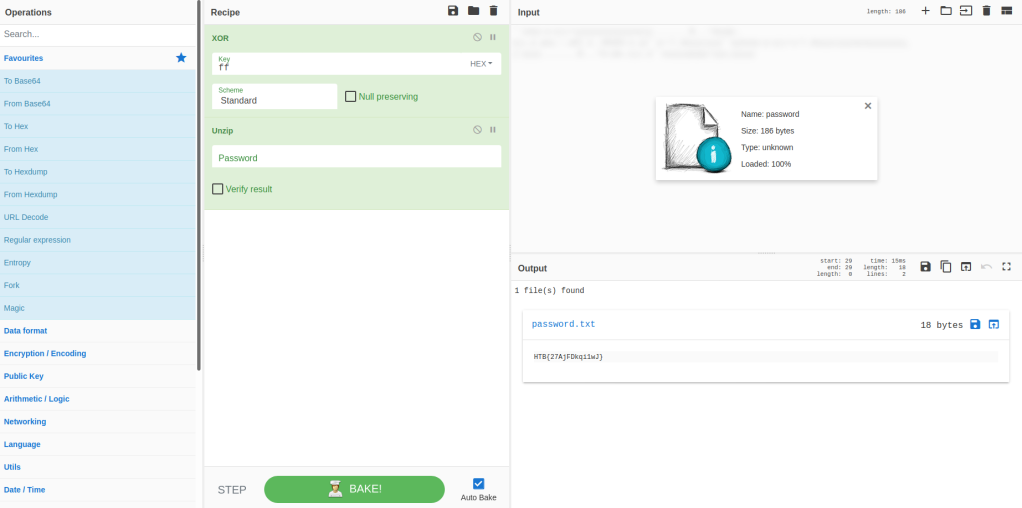
#4 “Crack the hash using rockyou and a cracking tool of your choice. What’s the password?“
Copy the hash and the salt to a file with the format is:
password$saltAnd use JohntheRipper and rockyou.txt to crack the hash.
john-the-ripper hash --format='dynamic=sha512($p.$s)' -w=rockyou.txtTask 3: Attack – Get back in!
#1 “The attacker defaced the website. What message did they leave as a heading?“
Access the webpage: http://10.10.175.129/

#2 “What’s the user flag?“
In Stream 3, we found that we can connect to ssh through port 2222.
ssh james@10.10.140.222 -p 2222Use the password we just found in task 2.
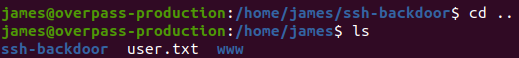
#3 “What’s the root flag?“
The hint is: “Did the attacker leave a quick way for them to get root again without a password?“
This is talked about a file named “.suid_bash” in /home/james and we can get root with:
./.suid_bash -p
We can get the explanation here.